Category: GBHackers
Let’s Encrypt, a leading certificate authority (CA) known for providing free SSL/TLS certificates since 2015, has issued its first-ever certificate…
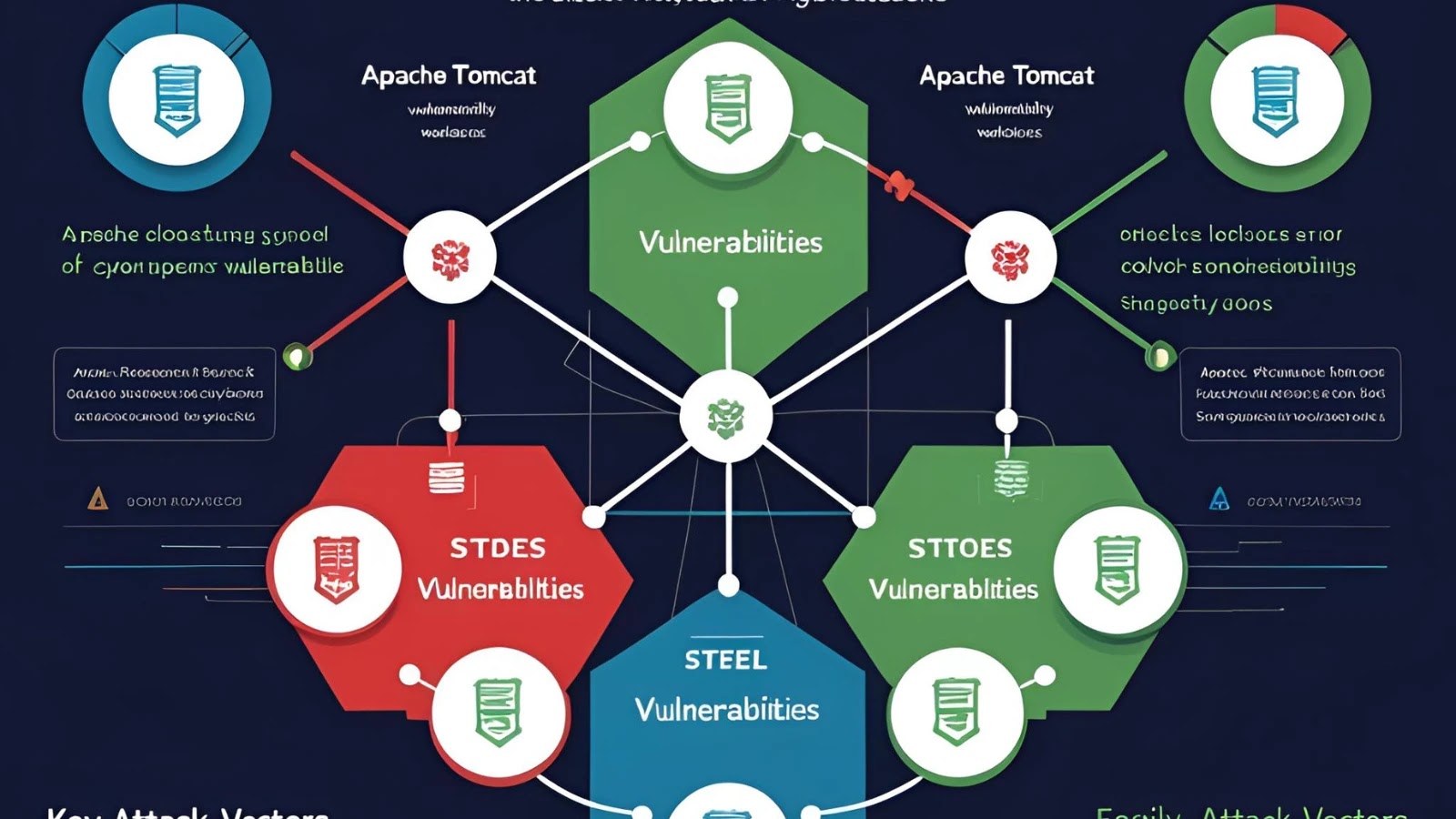
The Apache Foundation disclosed several critical vulnerabilities affecting two of its widely used software platforms, Apache Tomcat and Apache Camel,…
Token Security experts recently conducted a thorough investigation that exposed serious security weaknesses in Microsoft Azure’s Role-Based Access Control (RBAC)…
A sophisticated phishing campaign, initially spotlighted by Mexican journalist Ignacio Gómez Villaseñor, has evolved into a sprawling global threat, as…
NSFOCUS Fuying Lab’s Global Threat Hunting System has discovered a new botnet family called “hpingbot” that has been quickly expanding…
Threat actors have dramatically increased their exploitation of the cybersecurity sector, which is a disturbing development. Spain’s country code TLD,…
Citrix has issued an urgent advisory for NetScaler users following the release of builds 14.1.47.46 and 13.1.59.19, warning of potential…
Microsoft has officially confirmed that its recent Windows 11 update, KB5060829, is causing unexpected error entries in the Windows Firewall…
Dylan, 13, has accomplished a remarkable achievement by becoming the youngest security researcher to work with the Microsoft Security Response…
A new malware loader dubbed “BUBBAS GATE” has surfaced on underground forums and Telegram channels, drawing attention for its bold claims of…
The ongoing Russia-Ukraine conflict, which intensified in 2022, continues to reshape the cybercrime landscape in 2025, with hacktivism emerging as…
A new wave of cyber risk is emerging as AI-powered tools like ChatGPT and Perplexity become default search and answer…