Category: GBHackers
Let’s Encrypt, the world-renowned free Certificate Authority (CA), is on the verge of a significant milestone: issuing SSL/TLS certificates for…
The cyber threat group APT-C-36, widely known as Blind Eagle, has been orchestrating sophisticated cyberattacks targeting a range of sectors…
A novel social engineering technique dubbed “ClickFix” has surged by an alarming 517% between the second half of 2024 and…
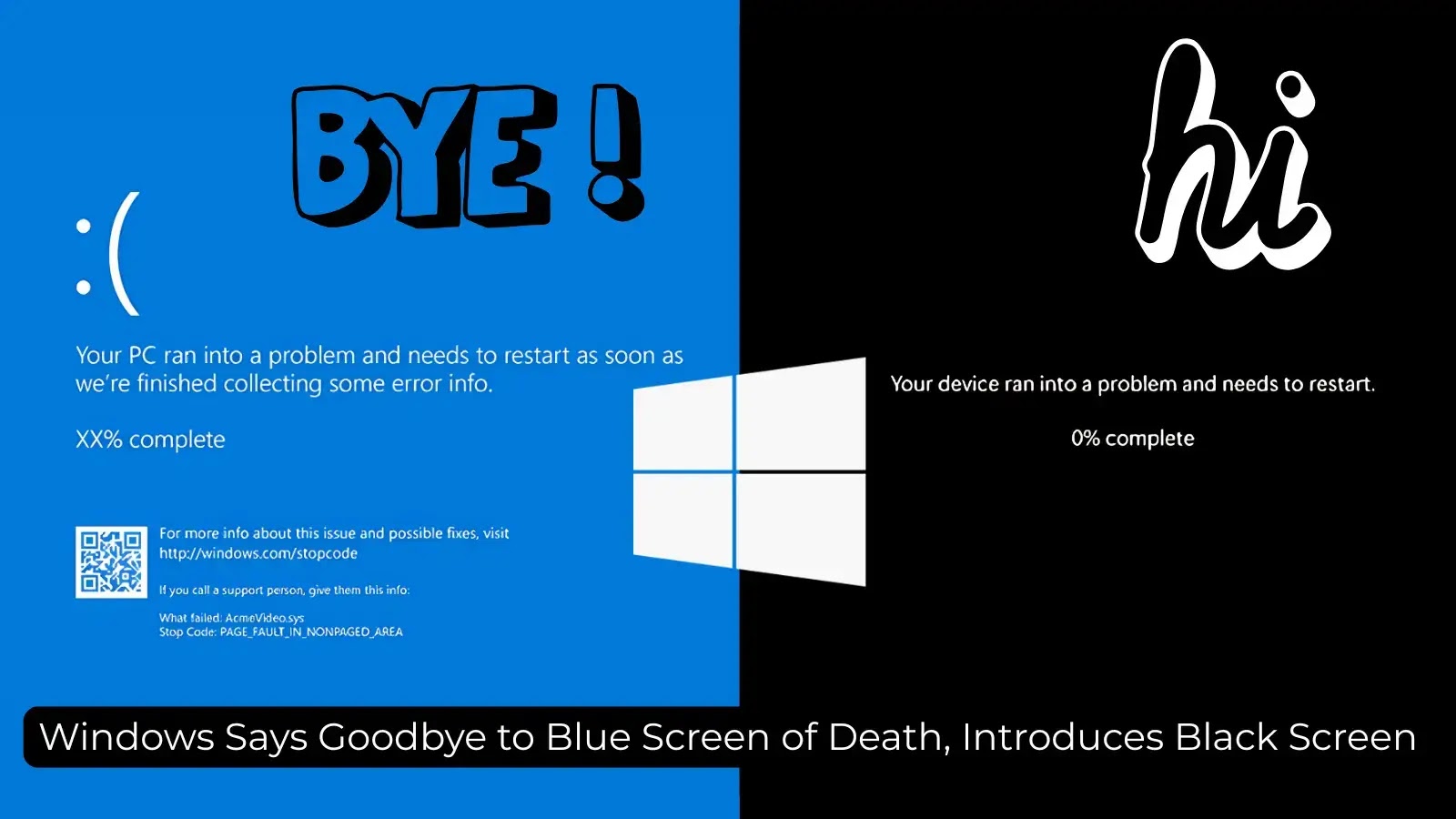
After nearly four decades as a symbol of frustration and failure for PC users worldwide, Microsoft is officially retiring the…
A critical security vulnerability has been discovered in multiple Mitsubishi Electric air conditioning systems, potentially allowing hackers to bypass authentication…
A 27-year-old former student of Western Sydney University has been charged with a string of cyber offences, following an extensive…
A critical pre-authentication vulnerability (CVE-2025-6709) in MongoDB Server enables unauthenticated attackers to trigger denial-of-service (DoS) conditions by exploiting improper input…
A Kansas City man has pleaded guilty to federal charges after admitting he hacked into the computer systems of multiple…
A newly disclosed critical vulnerability in the Open VSX Registry, the open-source marketplace for Visual Studio Code (VS Code) extensions,…
Researchers at BallisKit have introduced a sophisticated scenario within their MacroPack Pro tool to obfuscate and weaponize .NET assemblies, significantly…
A severe security flaw has been identified in IBM WebSphere Application Server, potentially allowing remote attackers to execute arbitrary code…
The Iranian threat group Educated Manticore, also tracked as APT35, APT42, Charming Kitten, or Mint Sandstorm, has intensified its cyber-espionage…