Category: GBHackers
The Iranian threat group Educated Manticore, also tracked as APT35, APT42, Charming Kitten, or Mint Sandstorm, has intensified its cyber-espionage…
A severe security flaw, dubbed nOAuth, has been identified in certain software-as-a-service (SaaS) applications integrated with Microsoft Entra ID, potentially…
CloudSEK’s TRIAD team has made the shocking discovery that the Androxgh0st botnet is a persistent and dynamic cyberthreat. It has…
Check Point Research has uncovered a renewed global spear-phishing campaign orchestrated by the Iranian threat actor Educated Manticore, also known…
Hewlett Packard Enterprise (HPE) has issued a critical security bulletin warning customers of a significant vulnerability in its OneView for…
Threat actors are increasingly leveraging the trusted names of popular software and services like ChatGPT, Cisco AnyConnect, Google Meet, and…
In a major breakthrough in the fight against cybercrime, U.S. and French authorities have charged and detained 25-year-old British national…
WhatsApp has announced the upcoming launch of “Message Summaries”—an AI-powered feature designed to help users quickly catch up on unread…
Cisco has issued urgent security patches addressing two critical vulnerabilities in its Identity Services Engine (ISE) and ISE Passive Identity…
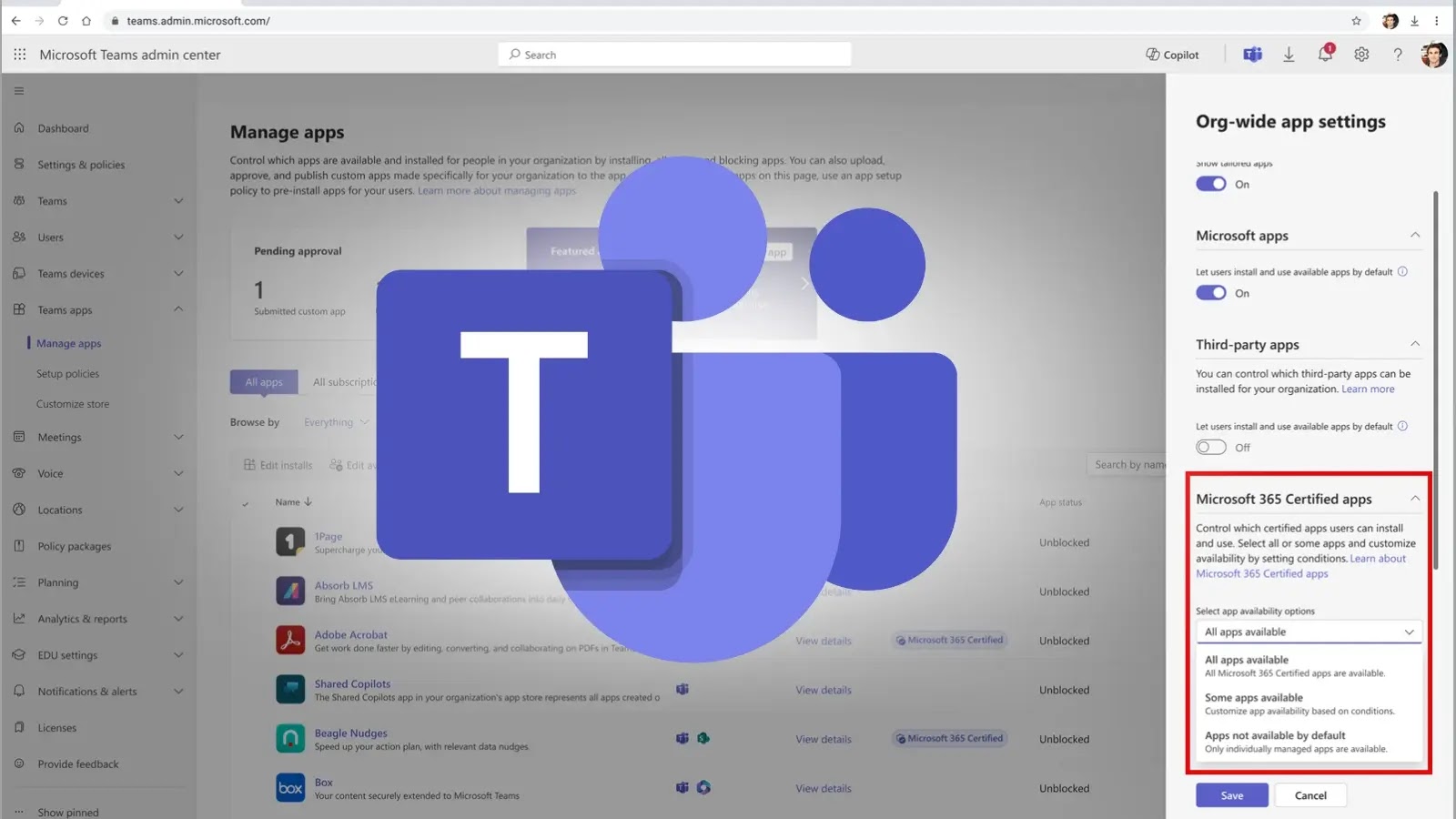
Microsoft is rolling out a major update to Microsoft Teams, empowering administrators with enhanced control over third-party app availability through…
Cybercriminals are increasingly leveraging large language models (LLMs) to amplify their hacking operations, utilizing both uncensored versions of these AI…
IBM X-Force researchers have uncovered a series of targeted cyberattacks orchestrated by the China-aligned threat actor Hive0154. Throughout 2025, this…