Category: GBHackers
A newly disclosed critical vulnerability in Dover Fueling Solutions’ ProGauge MagLink LX consoles has sent shockwaves through the global fuel…
A staggering 16 billion login credentials, usernames, and passwords have been exposed in what cybersecurity experts are calling the largest…
IBM has issued a critical security update for its QRadar SIEM platform after researchers uncovered multiple vulnerabilities, including a severe…
A new class of cyberattack is targeting organizations leveraging Atlassian’s Model Context Protocol (MCP), exposing a critical weakness in the…
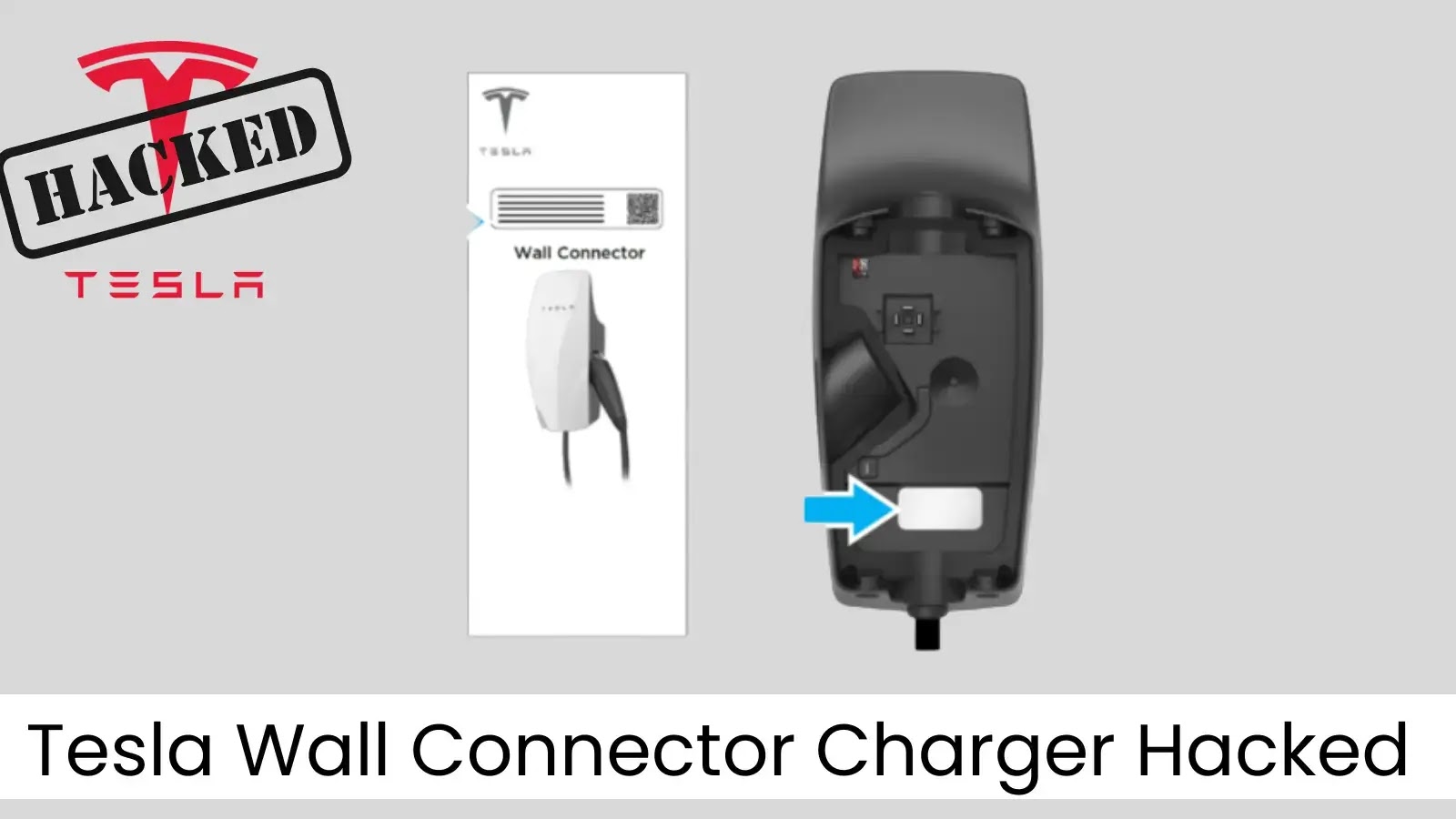
Security researchers from Synacktiv successfully hacked the Tesla Wall Connector through its charging port in just 18 minutes, exposing critical…
The North Korean state-sponsored threat actor group, identified as TA444 (also known as BlueNoroff, Sapphire Sleet, and others), has unleashed…
The Wordfence Threat Intelligence team identified a severe security flaw in the AI Engine plugin, a widely used tool installed…
The China-based advanced persistent threat (APT) group Silver Fox, also known as Void Arachne or The Great Thief of Valley,…
Minecraft, the wildly popular sandbox game with over 200 million monthly active players, has become the latest hunting ground for…
The global cybersecurity landscape is facing a seismic shift as the Qilin ransomware group, also known as Agenda, has surged…
Viasat Inc., a leading U.S. satellite and wireless communications provider, has been identified as the latest victim in a sweeping…
Our team stumbled upon a disturbing array of SpyNote spyware samples lurking in open directories across the internet. These misconfigured…