Category: GBHackers
Krispy Kreme Doughnut Corporation has confirmed a significant data breach that exposed the personal information of over 160,000 individuals following…
Security researchers from the Trellix Advanced Research Centre have uncovered a sophisticated malware campaign exploiting the widely trusted jQuery Migrate…
Proofpoint has uncovered a rebranded and significantly enhanced information stealer named Amatera Stealer, derived from the previously known ACR Stealer….
Seqrite Labs has uncovered a sophisticated variant of the Masslogger credential stealer malware being distributed through VBScript Encoded (.VBE) files….
The Golden SAML assault is a lesser-known but much more dangerous threat in a world where password-based hacks breach millions…
Google Threat Intelligence Group (GTIG), in collaboration with external partners, has uncovered a sophisticated phishing campaign orchestrated by a Russia…
A sophisticated malware campaign dubbed SERPENTINE#CLOUD has emerged, leveraging Cloudflare Tunnel infrastructure to deliver Python-based malware to Windows systems across…
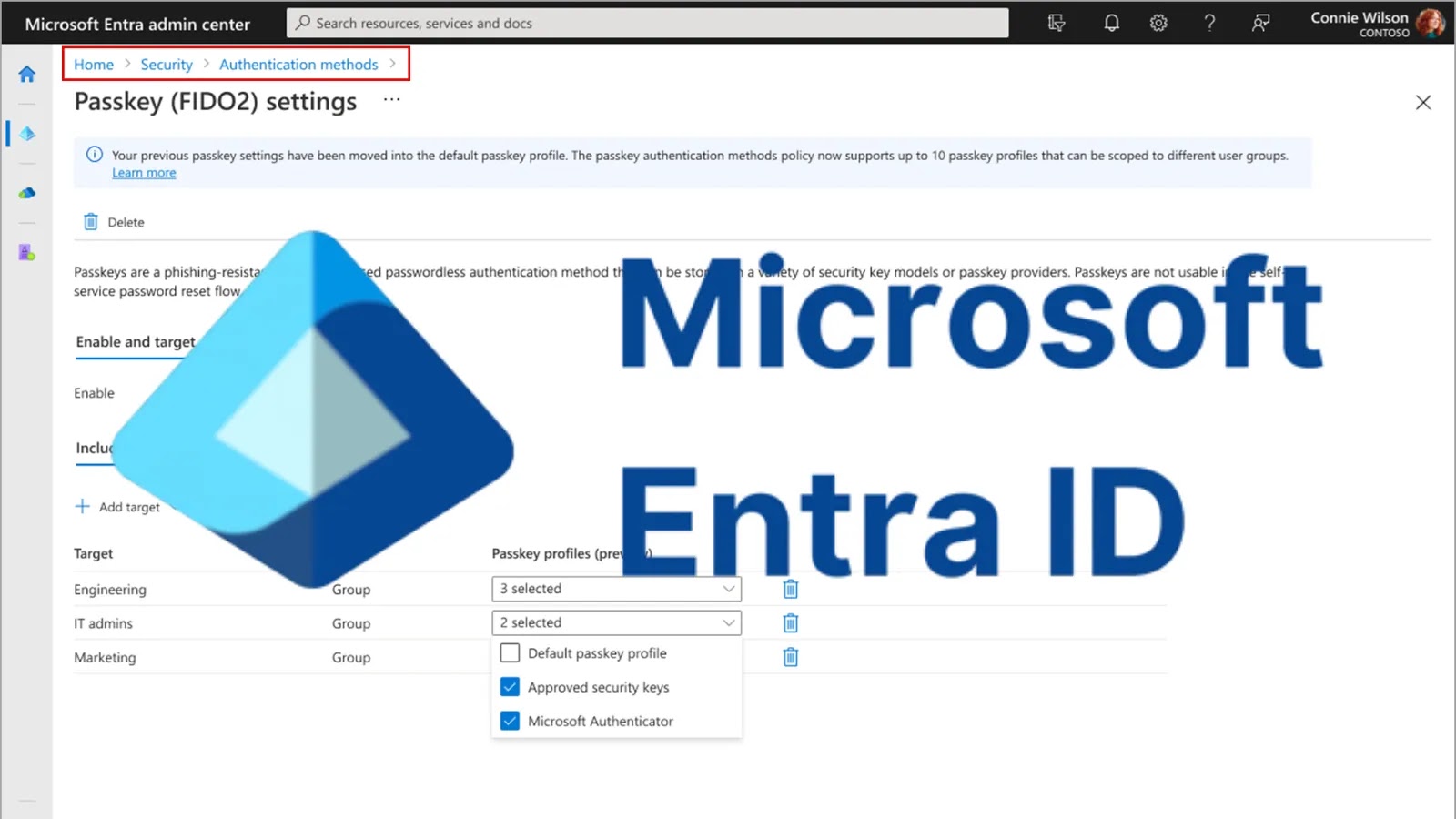
Microsoft has announced a significant update to its identity platform, Microsoft Entra ID, with the introduction of expanded passkey (FIDO2)…
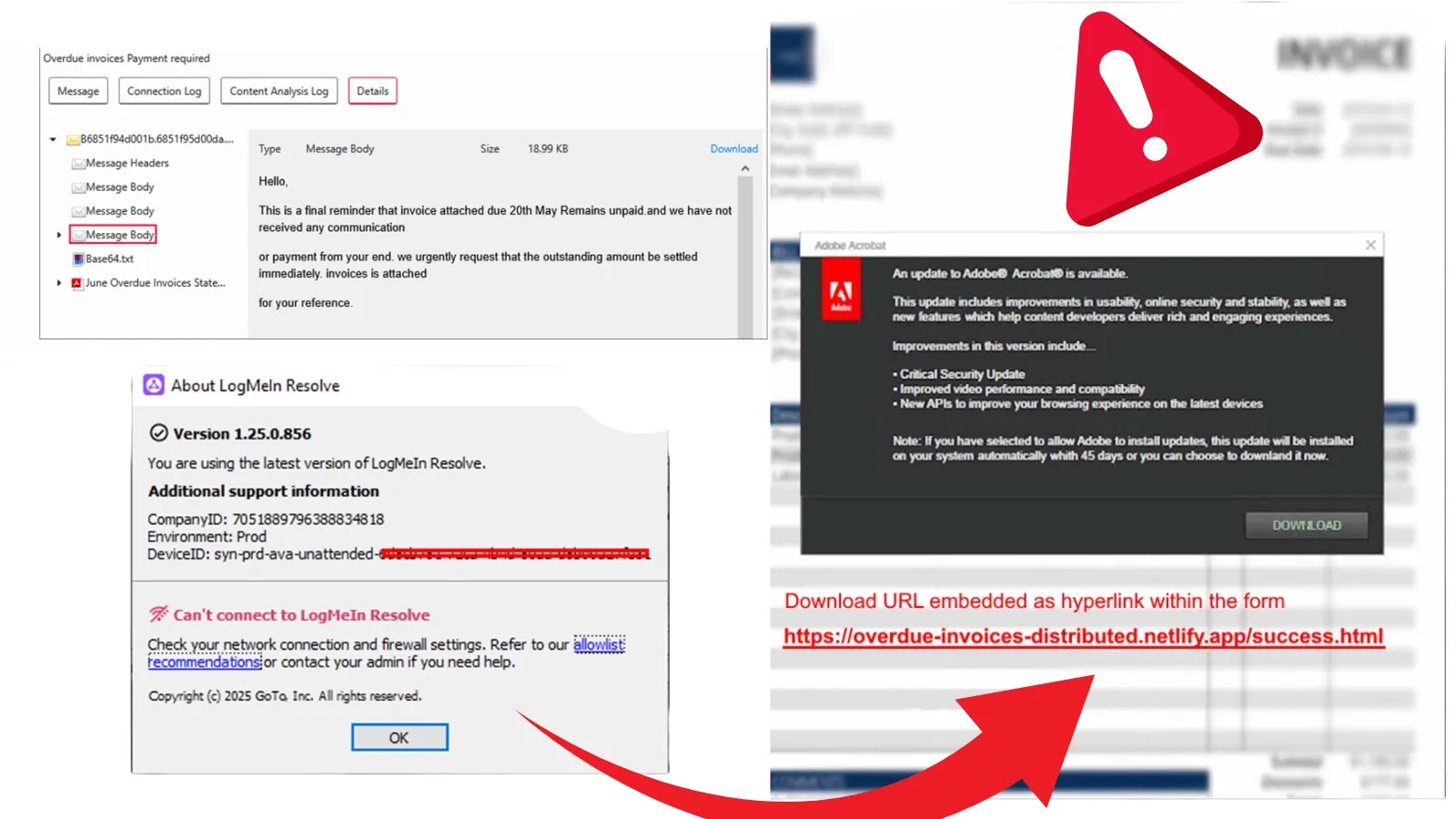
A sophisticated cyberattack campaign has been uncovered, leveraging LogMeIn Resolve remote access software to gain unauthorized control over user systems….
A newly disclosed vulnerability in Cisco’s AnyConnect VPN implementation for Meraki MX and Z Series devices poses a significant risk…
Thai authorities have dismantled a sophisticated criminal enterprise operating from the eight-storey Antai Holiday Hotel in Pattaya, unearthing both a…
A newly disclosed vulnerability in Apache Traffic Server (ATS) has raised serious concerns among enterprise users and cloud providers, as…