Category: GBHackers
A newly identified threat actor known as Water Curse has been linked to a sprawling campaign utilizing at least 76…
A series of newly disclosed critical vulnerabilities in the Sitecore Experience Platform (XP) have raised alarm across the enterprise technology…
A newly disclosed vulnerability in BeyondTrust’s Remote Support (RS) and Privileged Remote Access (PRA) products has raised alarms across the…
A new wave of cybercrime is exploiting the very backbone of internet trust: search engines. Recent research by Netcraft has…
Threat actors are leveraging deceptive tactics to distribute a fileless variant of AsyncRAT, a notorious remote access Trojan. Discovered during…
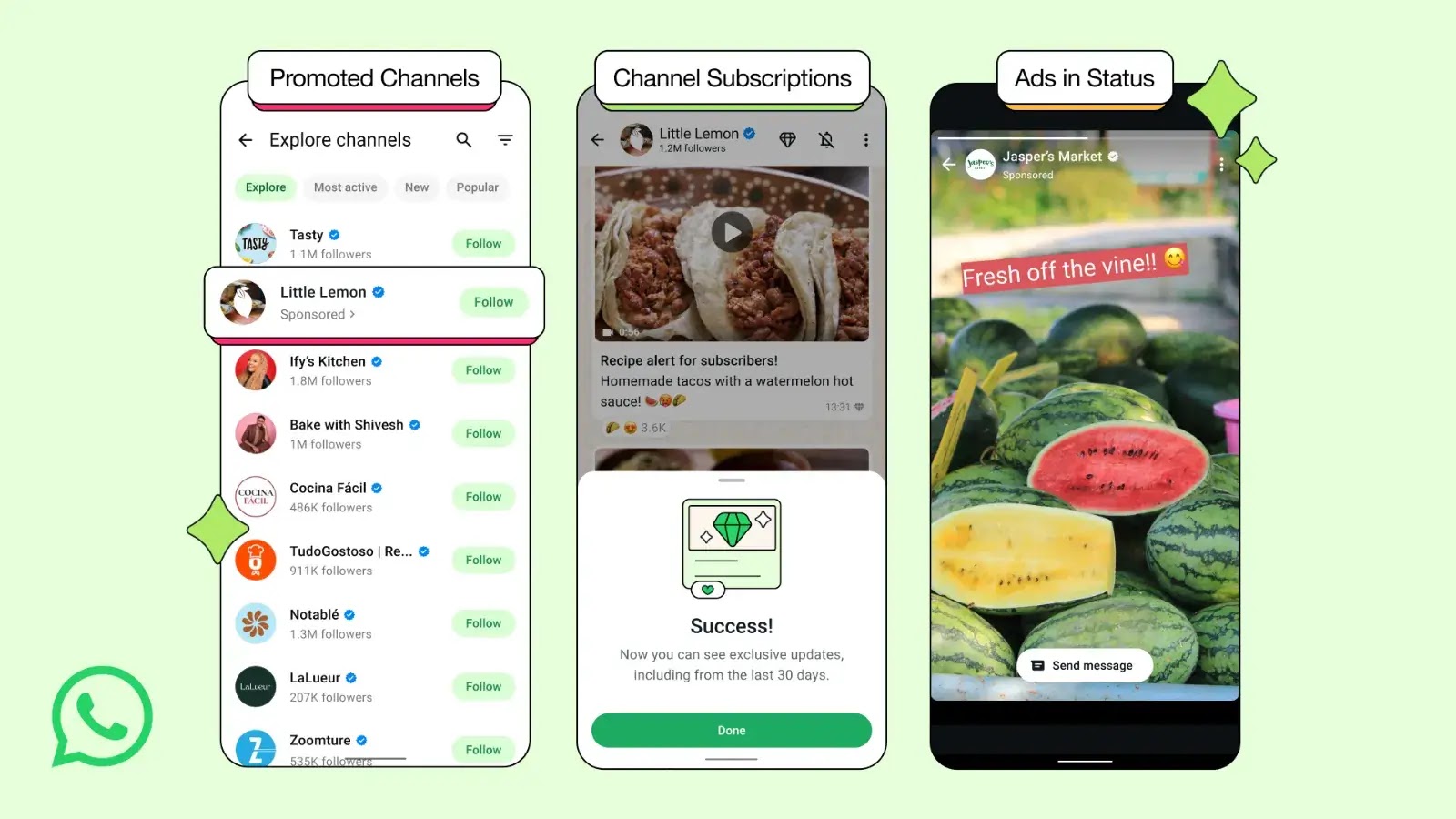
WhatsApp, the world’s most popular messaging app, is entering a new era as Meta officially begins rolling out advertisements within…
A critical vulnerability in ASUS’s popular Armoury Crate software has exposed millions of Windows users to the risk of system-level…
A newly discovered zero-day vulnerability in Google Chrome, tracked as CVE-2025-2783, is being actively exploited by hackers in sophisticated cyber-espionage…
Over 150,000 users across Google Play and the Apple App Store have fallen victim to a malicious SpyLoan application named…
Threat actors are increasingly exploiting legitimate channels to achieve privilege escalation, posing a severe risk to millions of devices worldwide….
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a high-priority alert following the discovery and active exploitation of…
A former intern at the UK’s intelligence agency GCHQ has been sentenced to seven and a half years in prison…