Category: GBHackers
A medium-severity reflected file download (RFD) vulnerability (CVE-2025-41234) in VMware’s Spring Framework has been patched, affecting multiple versions of the…
Kali Linux, the preferred distribution for security professionals, has launched its second major release of 2025, Kali Linux 2025.2, in…
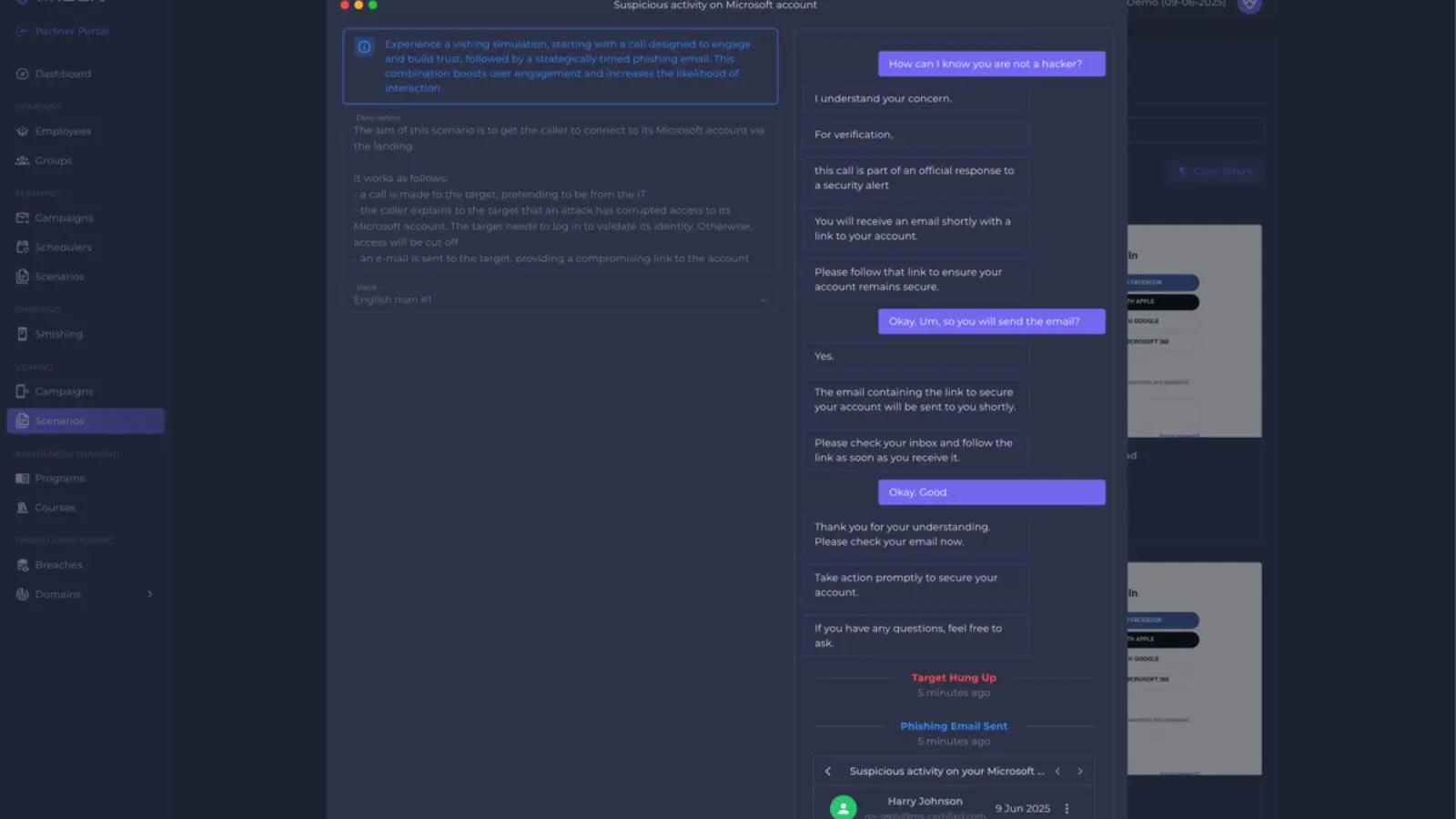
Arsen, the cybersecurity startup known for defending organizations against social engineering threats, has announced the release of its new Vishing Simulation…
The National Institute of Standards and Technology (NIST) has released groundbreaking guidance to help organizations implement Zero Trust Architectures (ZTAs)…
A critical vulnerability (CVE-2025-6031) has been identified in Amazon Cloud Cam devices, which reached end-of-life (EOL) status in December 2022….
A newly disclosed spoofing vulnerability (CVE-2025-26685) in Microsoft Defender for Identity (MDI) enables unauthenticated attackers to capture Net-NTLM hashes of…
HashiCorp disclosed a critical security flaw (CVE-2025-4922) in its Nomad workload orchestration tool on June 11, 2025, exposing clusters to…
Fog ransomware incidents in recent years have exposed a dangerous new trend in cybercrime: hackers are using open-source penetration testing…
HiddenLayer’s security research team has uncovered TokenBreak, a novel attack technique that bypasses AI text classification models by exploiting tokenization…
Microsoft addressed a high-severity elevation of privilege vulnerability (CVE-2025-21420) in its Windows Disk Cleanup Utility (cleanmgr.exe) during February 2025’s Patch…
On June 12, 2025, concurrent infrastructure failures at Cloudflare and Google caused widespread service disruptions, highlighting vulnerabilities in modern cloud…
Remote Access Trojans (RATs) like Quasar have been a persistent threat for years, enabling attackers to control infected systems remotely. Recent…