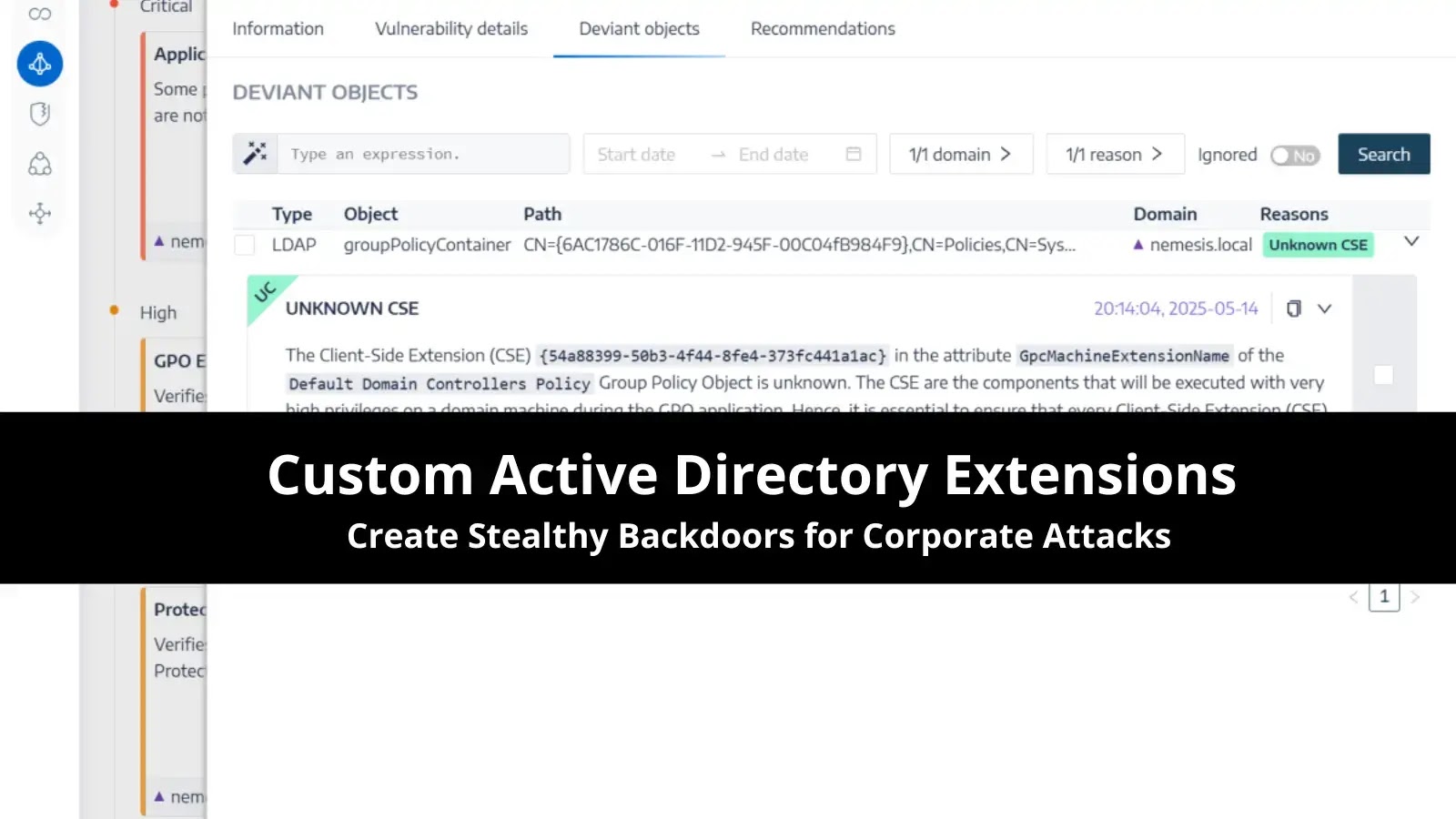
Category: GBHackers
Active Directory (AD) Group Policy Objects (GPOs) are a cornerstone of centralized management for Windows environments, enabling administrators to configure…
Since 2016, the “DollyWay World Domination” campaign has quietly compromised more than 20,000 WordPress websites worldwide, exploiting vulnerabilities in plugins…
A critical improper authentication vulnerability has been discovered in ConnectWise ScreenConnect, tracked as CVE-2025-3935 and mapped to CWE-287 (Improper Authentication)….
The North Face, a prominent outdoor fashion brand under VF Outdoor, LLC, detected unusual activity on its website, thenorthface.com. Following…
The Android Security Bulletin for June 2025, published on June 2, details a series of high-severity vulnerabilities affecting a wide…
The manufacturing sector has emerged as a prime target for cyber attackers in 2024, with a staggering 71% surge in…
Cybersecurity researchers have shed light on the often-underestimated vulnerabilities in containerized environments, emphasizing the critical role of host-based log analysis…
A new and insidious threat has surfaced in the cybersecurity landscape as Darktrace’s Threat Research team uncovers PumaBot, a Go-based…
A pro-Ukrainian hacktivist group known as BO Team, also operating under aliases such as Black Owl, Lifting Zmiy, and Hoody…
In a chilling revelation for cybersecurity professionals, the Russian Market has solidified its position as the leading hub for stolen…
Aembit, the workload identity and access management (IAM) company, today announced a major expansion of its platform to support Microsoft…
A severe vulnerability in Apple’s iOS activation infrastructure has been uncovered, posing a significant risk to device security during the…