Category: GBHackers
As part of its ongoing commitment to product security, Dell Technologies has released a significant update for the PowerStore T…
Security Information and Event Management (SIEM) platforms are essential for detecting, analyzing, and responding to cybersecurity threats in real time….
The hacker group UTG-Q-015, first identified in December 2024 for mounting attacks on major websites like CSDN, has escalated its…
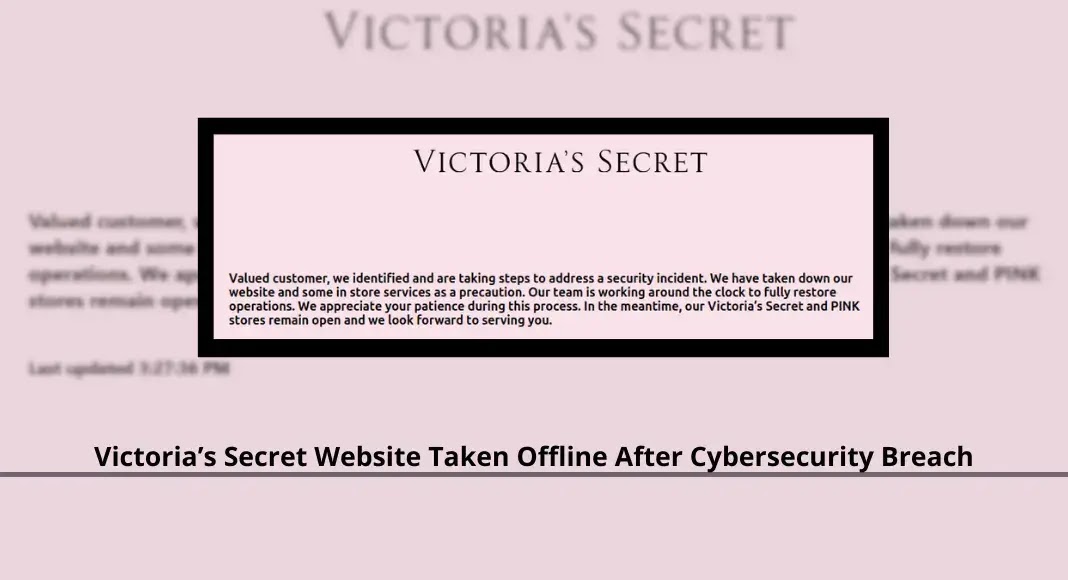
Victoria’s Secret, the iconic lingerie retailer, has taken its US website offline and suspended some in-store services following a major…
Trellix’s email security systems detected a highly targeted spear-phishing campaign aimed at CFOs and finance executives across industries like banking,…
Operant AI has announced the release of Woodpecker, an open-source automated red teaming engine designed to make advanced security testing…
GreyNoise Research has publicly disclosed a sophisticated cyberattack campaign that has compromised over 9,000 ASUS routers worldwide. First detected by…
Google Threat Intelligence Group (GTIG), a sophisticated malware campaign dubbed “TOUGHPROGRESS” has been uncovered, orchestrated by the notorious PRC-based threat…
Mandiant Threat Defense has uncovered a malicious campaign orchestrated by the threat group UNC6032, which capitalizes on the global fascination…
Citrix has issued a high-severity security bulletin addressing multiple vulnerabilities—CVE-2025-27462, CVE-2025-27463, and CVE-2025-27464—affecting XenServer VM Tools for Windows. These vulnerabilities…
Russia’s GRU-backed APT28, widely known as Fancy Bear, has intensified its cyber espionage campaign against NATO-aligned organizations. Active since at…
Cybersecurity researchers at Trend Research have uncovered the aggressive operations of Earth Lamia, an Advanced Persistent Threat (APT) group with…