Category: GBHackers
A critical vulnerability, identified as CVE-2025-0072, has been discovered in the Arm Mali GPU driver, posing a significant threat to…
A groundbreaking study from Tsinghua University and Zhongguancun Laboratory has uncovered critical vulnerabilities in modern web infrastructure, revealing that HTTP/2…
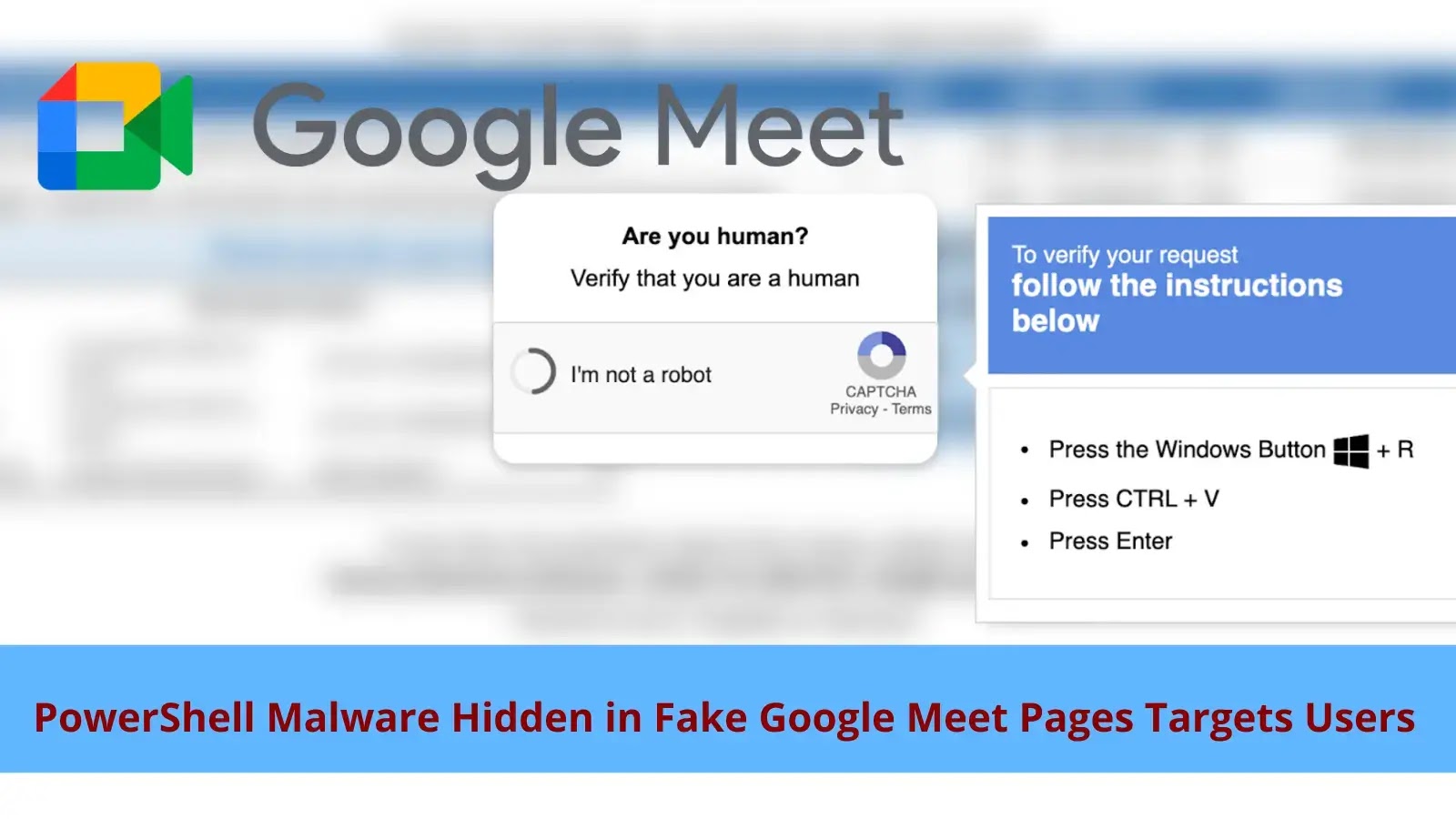
A new wave of cyberattacks exploits user trust in Google Meet by deploying meticulously crafted fake meeting pages that trick…
Cybersecurity experts have noted an increase in data breaches where threat actors are directly querying internal databases to steal sensitive…
Katz Stealer has emerged as a potent credential-stealing malware-as-a-service, targeting popular web browsers such as Chrome, Edge, Brave, and Firefox….
Threat actors have been exploiting the trust in India’s digital public infrastructure by setting up a deceptive phishing site, digiyatra[.]in,…
The Federal Bureau of Investigation (FBI) has issued a critical alert regarding the escalating activities of the cyber threat actor…
ChatGPT has rolled out a beta feature called Deep Research Connectors, designed to integrate seamlessly with third-party applications such as…
A hackers has made news by allegedly selling a ZIP archive containing more than 500 compromised databases, which seems to…
ONEKEY Research Lab has uncovered a severe command injection vulnerability in the MeteoBridge firmware, a compact device designed to connect…
A Socket’s Threat Research Team has revealed a sophisticated and ongoing campaign targeting the npm ecosystem, involving 60 malicious packages…
A decade-long cyber espionage campaign orchestrated by the advanced persistent threat (APT) group TA-ShadowCricket has been exposed through a joint…