Category: GBHackers
A Socket’s Threat Research Team has revealed a sophisticated and ongoing campaign targeting the npm ecosystem, involving 60 malicious packages…
A decade-long cyber espionage campaign orchestrated by the advanced persistent threat (APT) group TA-ShadowCricket has been exposed through a joint…
Cybersecurity firm LayerX has uncovered over 40 malicious Chrome browser extensions, many of which are still available on the Google…
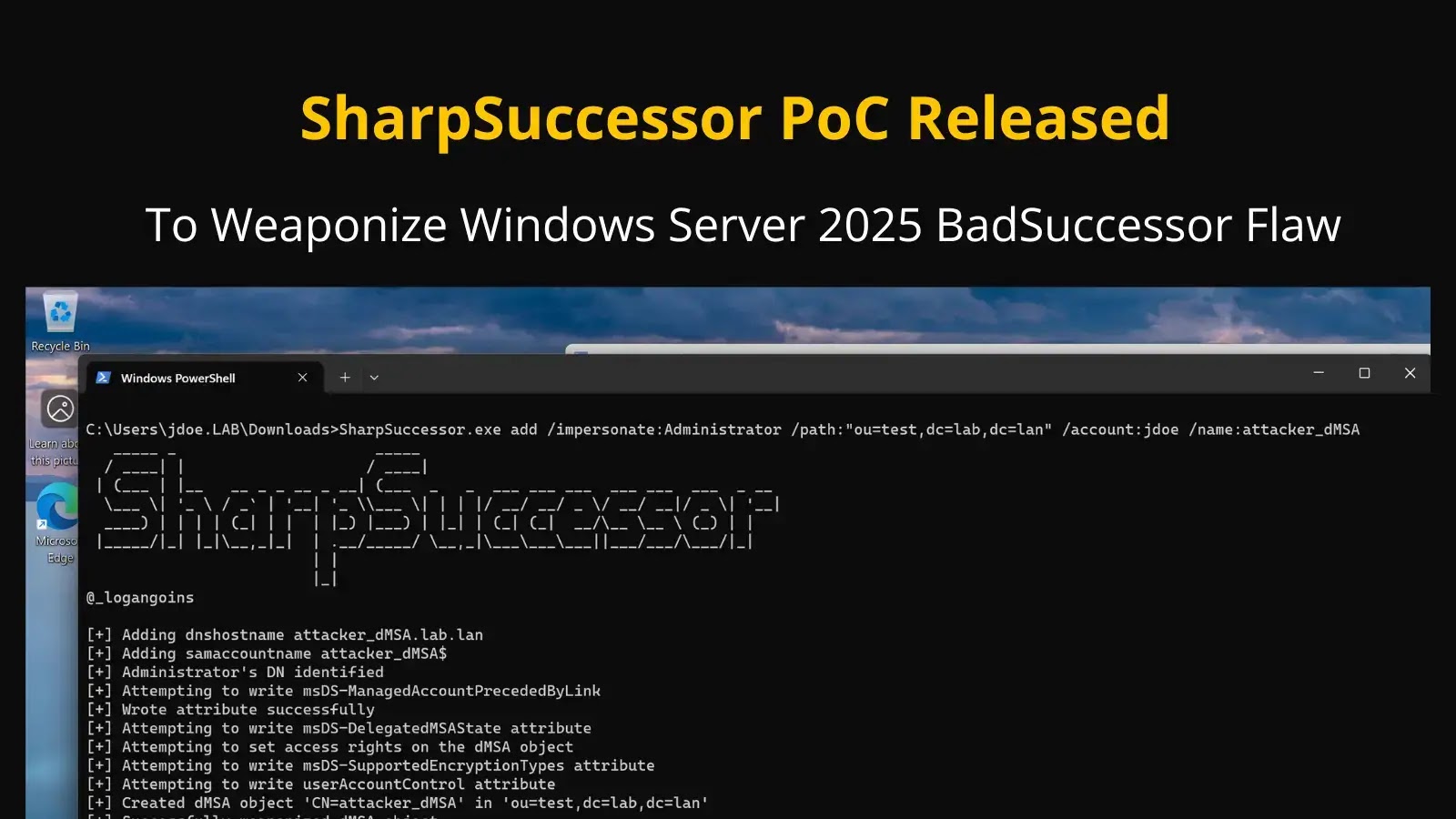
A critical privilege escalation vulnerability in Windows Server 2025’s delegated Managed Service Account (dMSA) feature enables attackers to compromise Active…
Oracle has addressed a significant security flaw in its Transparent Network Substrate (TNS) protocol, used for database communications, with the…
A newly discovered vulnerability in vBulletin, one of the world’s most popular commercial forum platforms, has highlighted the dangers of…
OpenAI’s latest and most advanced artificial intelligence model, codenamed “o3,” has sparked alarm in the AI safety community after researchers…
Nova Scotia Power, the largest electricity provider in the province, confirmed on Friday, May 23, 2025, that it has been…
The Linux 6.15 kernel, released on May 25, 2025, marks a pivotal moment in open-source development, introducing several groundbreaking features…
A recently disclosed vulnerability (CVE-2025-46176) exposes critical security flaws in D-Link’s DIR-605L and DIR-816L routers, revealing hardcoded Telnet credentials that…
Tenable has released version 6.5.1 of its Network Monitor, a key passive vulnerability scanning solution, to address several high-severity vulnerabilities…
A critical security vulnerability, tracked as CVE-2025-24813, has been discovered in Apache Tomcat, a widely used open-source Java servlet container…