Category: GBHackers
Group123, a North Korean state-sponsored Advanced Persistent Threat (APT) group also known by aliases such as APT37, Reaper, and ScarCruft,…
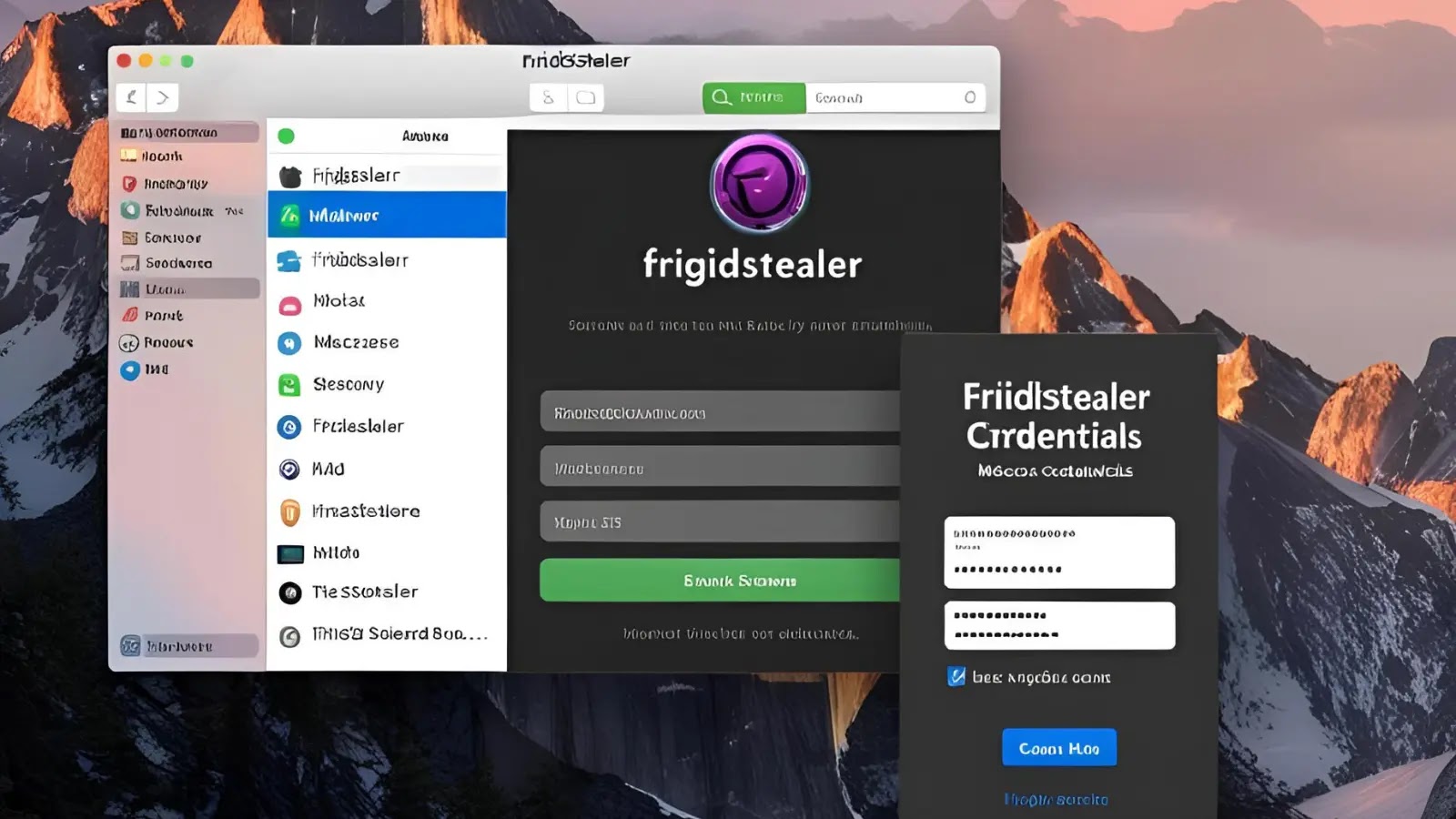
An macOS users, a new information-stealing malware dubbed FrigidStealer has emerged as a formidable threat since January 2025. This insidious…
Federal Bureau of Investigation has issued a warning about an ongoing malicious messaging campaign targeting current and former senior US…
Jenkins, the widely used automation server for CI/CD pipelines, has released a critical security advisory addressing several vulnerabilities in popular…
SonicWall has issued a critical security advisory (SNWLID-2025-0010) for its SMA1000 Appliance Work Place interface, revealing a high-severity Server-Side Request…
Security researchers successfully illustrated significant vulnerabilities across several platforms on the first day of Pwn2Own Berlin 2025, taking home a…
Cybersecurity researchers have uncovered a growing trend in which threat actors are exploiting Microsoft PowerShell a legitimate Windows command-line interface…
Tor Project has unveiled oniux, a new command-line utility that provides comprehensive network isolation for Linux applications, ensuring all traffic…
Cybersecurity giant Proofpoint has announced its agreement to acquire Hornetsecurity Group, a leading European provider of AI-powered Microsoft 365 security…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding five zero-day vulnerabilities affecting multiple Fortinet…
Major victory against online crime, two of the world’s largest illicit marketplaces-Huione Guarantee (also known as “Haowang Guarantee”) and Xinbi…
The Socket Threat Research Team has uncovered a surge in supply chain attacks where threat actors weaponize open source software…