Category: GBHackers
Broadcom-owned VMware has released security patches addressing a moderate severity insecure file handling vulnerability in VMware Tools, tracked as CVE-2025-22247…
Cybersecurity developers have released a new tool called “defendnot,” a successor to the previously DMCA-takedown-affected “no-defender” project. This innovative utility…
Microsoft’s Copilot for SharePoint, designed to streamline enterprise collaboration through generative AI, has become an unexpected weapon for cybercriminals targeting…
The open-source penetration testing toolkit Metasploit has unveiled a major update, introducing four new modules, including a highly anticipated exploit…
A sophisticated and highly coordinated cyberattack campaign came to light, as tracked by Guardz Research. This operation zeroed in on…
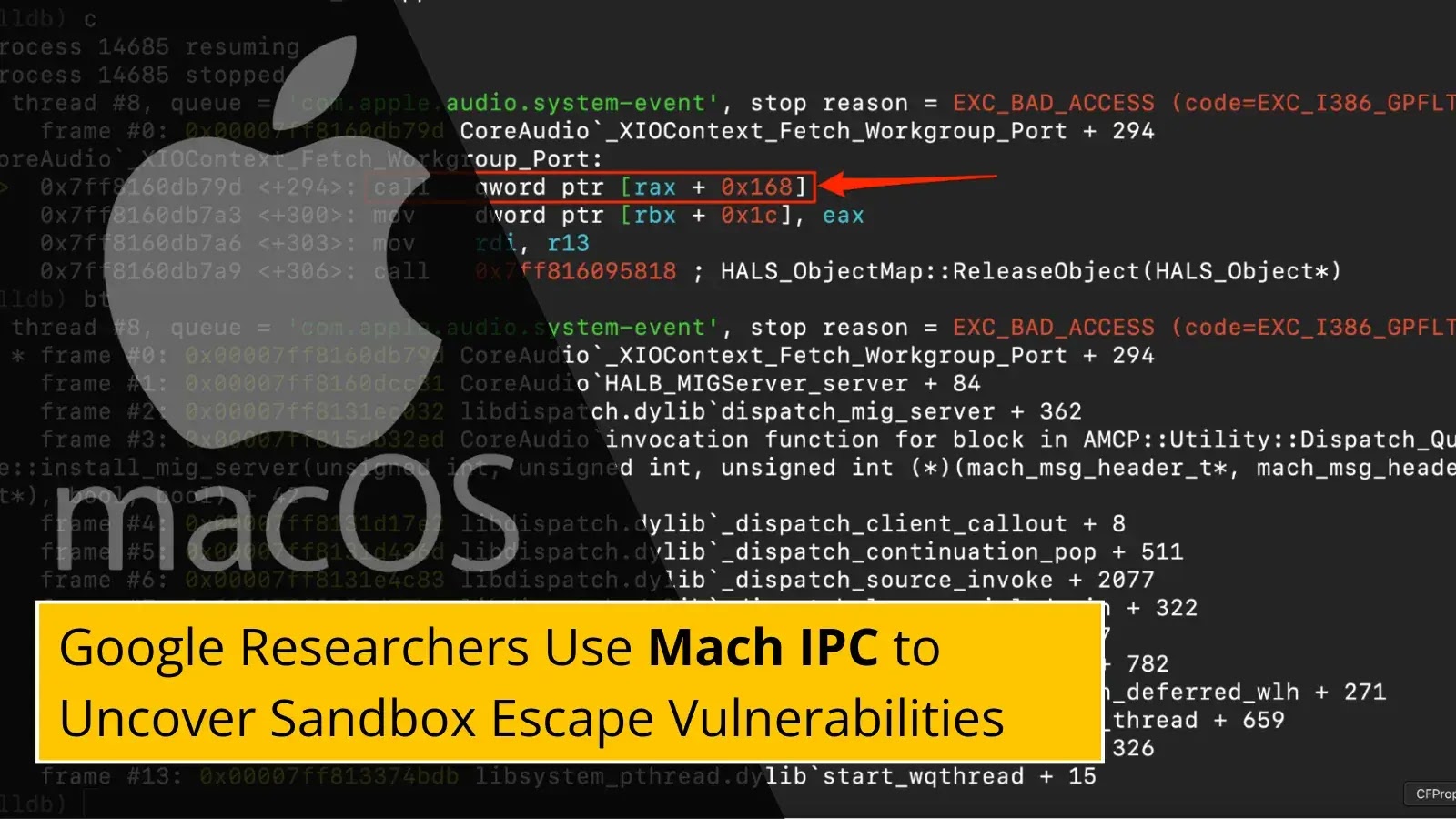
Google Project Zero researchers have uncovered new sandbox escape vulnerabilities in macOS using an innovative approach that leverages Mach Interprocess…
A chilling new ransomware attack method has emerged, with hackers exploiting innocuous JPEG image files to deliver fully undetectable (FUD) ransomware,…
Microsoft has announced the upcoming release of a groundbreaking “Prevent Screen Capture” feature for Teams, designed to block unauthorized screenshots…
A novel exploit method leveraging Beacon Object Files (BOFs) has emerged, enabling attackers to extract Microsoft Entra (formerly Azure AD)…
Google has integrated artificial intelligence into its cybersecurity toolkit to shield users from financial and data theft scams. On Friday,…
Kyle Schutt, a 37-year-old DOGE employee identified in federal payroll records, has had his personal email address and associated passwords…
Bluetooth SIG’s decision to transition to a bi-annual release cadence marks a strategic pivot toward fostering rapid iteration and market…