Category: GBHackers
The Darcula group has orchestrated a massive phishing-as-a-service (PhaaS) operation, dubbed Magic Cat, compromising an estimated 884,000 credit card details…
Landmark organizational shift, OpenAI announced its transition from a capped-profit LLC to a Public Benefit Corporation (PBC) while maintaining governance…
Google has significantly expanded the capabilities of NotebookLM, its AI-powered research tool, by introducing Audio Overviews in more than 50…
Hackers are leveraging a sophisticated social engineering technique dubbed “ClickFix” to trick Windows users into executing malicious scripts on their…
A newly identified cyberattack campaign has surfaced, leveraging the recognizable branding of India’s Ministry of Defence to distribute cross-platform malware…
Target application included a username field restricted by a frontend regex filter (/^[a-zA-Z0-9]{1,20}$/), designed to accept only alphanumeric characters. While…
Security researchers have released GPOHound, a powerful open-source tool designed to analyze Group Policy Objects (GPOs) in Active Directory environments for…
A newly discovered pre-authentication denial-of-service (DoS) vulnerability in Microsoft’s Windows Deployment Services (WDS) exposes enterprise networks to instant system crashes via malicious…
The Cybersecurity and Infrastructure Security Agency (CISA) issued an urgent alert regarding an actively exploited vulnerability in Langflow, a popular…
A critical vulnerability has been uncovered in Microsoft’s Telnet Client (telnet.exe), enabling attackers to steal Windows credentials from unsuspecting users,…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
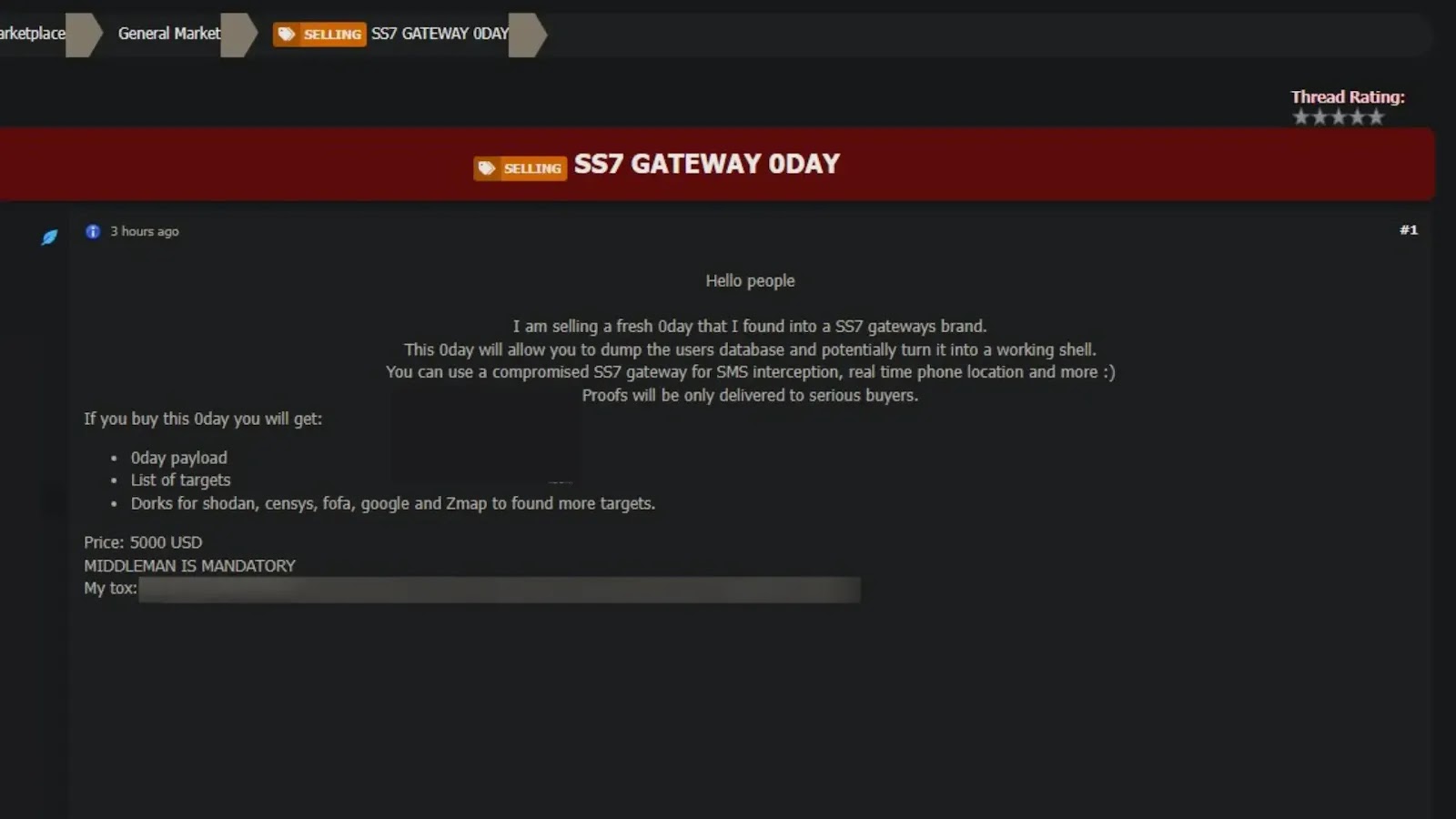
A newly discovered dark web listing claims to sell a critical SS7 protocol exploit for $5,000, raising alarms about global…