Category: GBHackers
Leading cryptocurrency exchange Kraken has disclosed that it recently thwarted an infiltration attempt by a suspected North Korean hacker posing…
A high-severity vulnerability (CVE-2025-46762) has been discovered in Apache Parquet Java, exposing systems using the parquet-avro module to remote code…
Cybersecurity researchers are raising alarms as hackers increasingly weaponize email input fields to execute cross-site scripting (XSS) and server-side request forgery (SSRF) attacks. These…
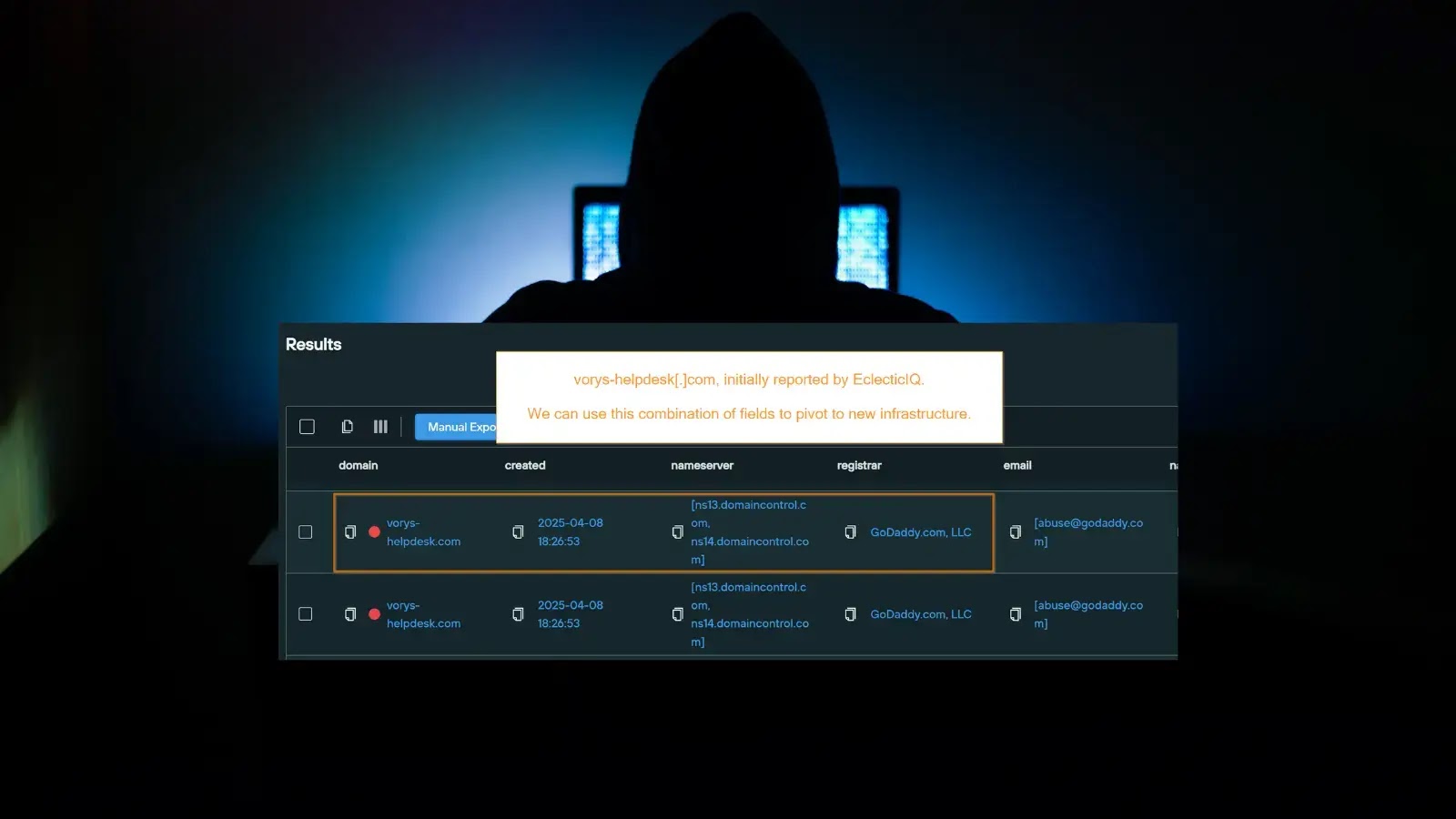
A recent investigation by cybersecurity firm EclecticIQ, in collaboration with threat hunters, has exposed a surge in malicious activity tied…
A researcher has unveiled a novel integration between AI-powered Copilot and Microsoft’s WinDbg, dramatically simplifying Windows crash dump analysis. For…
Cybersecurity researchers have uncovered a dangerous new exploitation technique, dubbed the “SonicBoom Attack Chain,” which allows hackers to bypass authentication…
National Cyber Security Centre (NCSC) has issued technical guidance following a series of cyber attacks targeting UK retailers. These incidents…
Claude AI, developed by Anthropic, has been exploited by malicious actors in a range of adversarial operations, most notably a…
As Tax Day on April 15 approaches, a alarming cybersecurity threat has emerged targeting U.S. citizens, according to a detailed…
Insikt Group has uncovered two new malware families, TerraStealerV2 and TerraLogger, attributed to the notorious financially motivated threat actor Golden…
Global cybersecurity landscape is undergoing a significant transformation, as state-sponsored hacktivism gains traction amid ongoing conflicts. In 2024, Forescout Technologies…
North Korean nationals have successfully infiltrated the employee ranks of major global corporations at a scale previously underestimated, creating a…