Category: GBHackers
Cybersecurity researchers have discovered a sophisticated phishing-as-a-service (PhaaS) platform, dubbed “Morphing Meerkat,” that leverages DNS mail exchange (MX) records to…
A critical SQL injection vulnerability, tracked as CVE-2025-24799, has been identified in GLPI, a widely used open-source IT Service Management (ITSM) tool….
Deep learning models, increasingly integral to safety-critical systems like self-driving cars and medical devices, are vulnerable to stealthy backdoor attacks….
Elastic Security Labs has uncovered a sophisticated malware campaign, dubbed REF8685, targeting the Iraqi telecommunications sector. The campaign utilizes a…
In a complex cyber operation discovered by Silent Push Threat Analysts, Russian hackers have launched a multi-pronged phishing campaign impersonating…
Forescout Vedere Labs has uncovered 46 new vulnerabilities in solar power systems, primarily affecting inverters from three leading manufacturers Sungrow,…
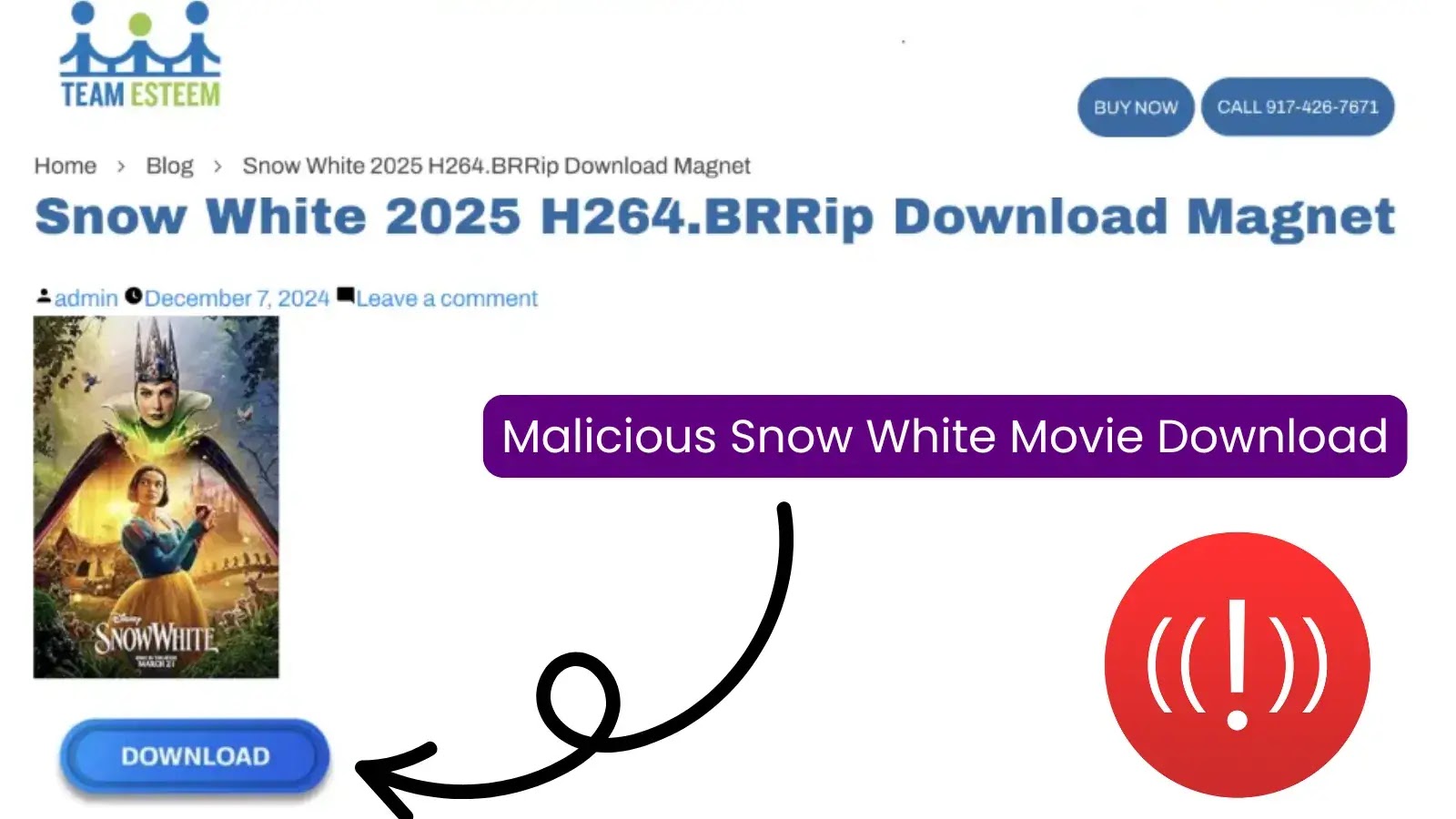
As the latest adaptation of Snow White hits theaters with lukewarm reception, the absence of streaming options on platforms like…
A recent scoping review has revealed that red team tactics are becoming increasingly sophisticated as artificial intelligence (AI) technologies advance….
Cybercriminals are increasingly targeting MailChimp, a popular email marketing platform, through sophisticated phishing and social engineering attacks. Recent incidents reveal…
Meta AI has announced its rollout across 41 European countries. This development marks a critical step in the company’s mission…
Cloudflare has contributed to the open-sourcing of OPKSSH, a tool that integrates single sign-on (SSO) technologies like OpenID Connect (OIDC)…
The Tor Project has swiftly released an emergency update for the Tor Browser, 14.0.8, which is exclusively available for Windows…