Category: GBHackers
Kuala Lumpur International Airport (KLIA), one of Southeast Asia’s busiest airports, was hit by a major cyberattack over the weekend….
A new ransomware strain, PlayBoy LOCKER, has been identified targeting Windows, NAS, and ESXi systems. First discovered in September 2024…
Classiscam, an automated scam-as-a-service operation, has been identified as a significant threat in Central Asia, leveraging sophisticated techniques to defraud…
Resecurity, a prominent cybersecurity firm, has successfully exploited a vulnerability in the Data Leak Site (DLS) of Blacklock Ransomware, gaining…
A sophisticated phishing campaign targeting the hospitality industry has been uncovered, with threat actors impersonating Booking.com to gain access to…
ESET researchers have connections between the newly emerged ransomware-as-a-service (RaaS) group RansomHub and established ransomware gangs, including Play, Medusa, and…
INE, a global leader in networking and cybersecurity training and certifications, is proud to announce it is the recipient of…
A large-scale cyberattack has compromised approximately 150,000 legitimate websites by injecting malicious JavaScript to redirect visitors to Chinese-language gambling platforms….
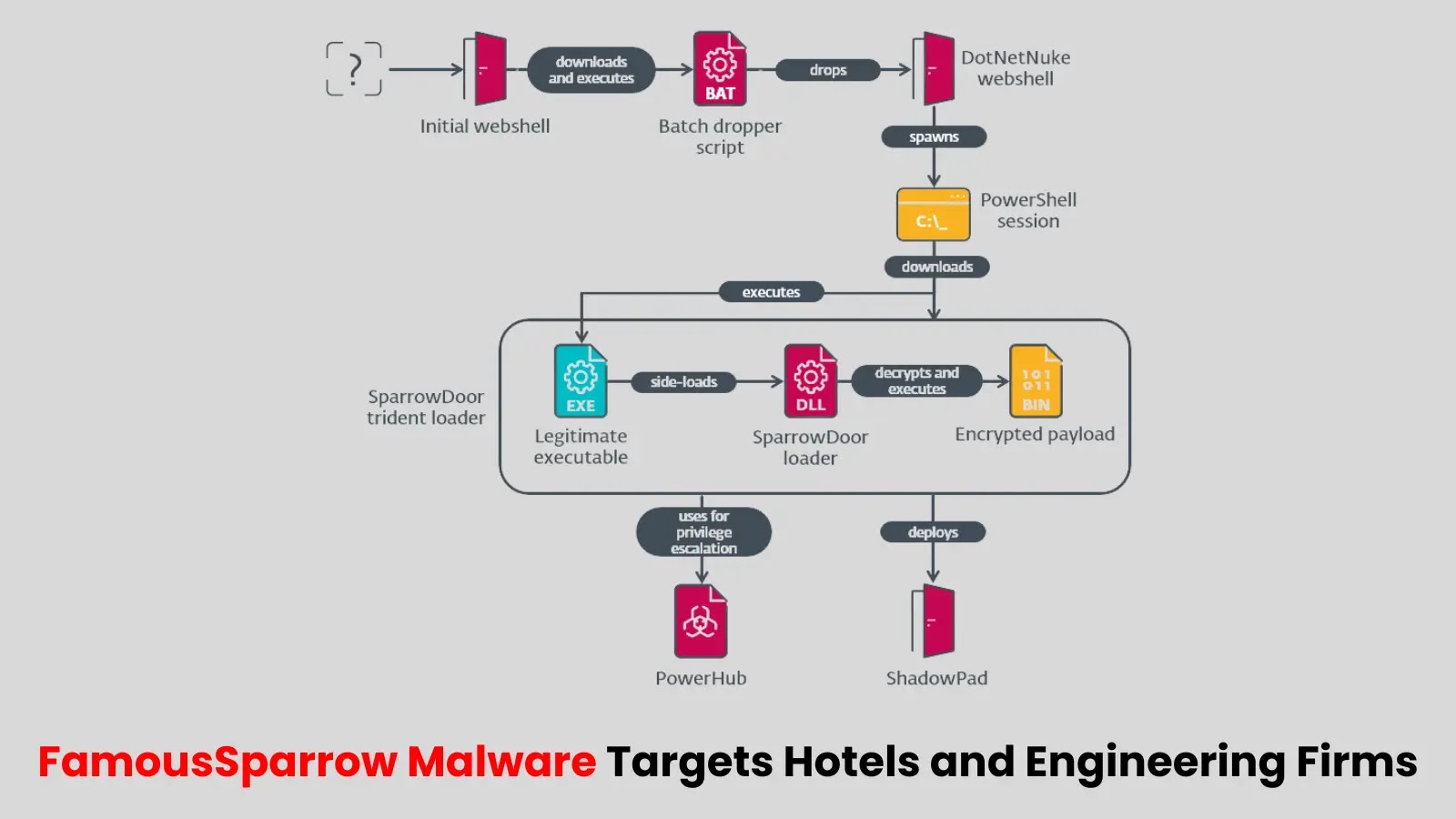
ESET researchers have uncovered new activity from the China-aligned APT group FamousSparrow, revealing two previously undocumented versions of their custom…
A recent investigation by DomainTools Investigations (DTI) has uncovered a massive phishing infrastructure targeting defense and aerospace entities, particularly those…
A major cybersecurity incident has struck the New South Wales court system, as cybercrime detectives investigate a significant data breach…
The cybersecurity landscape has been disrupted by the emergence of Lucid, a sophisticated Phishing-as-a-Service (PhAAS) platform developed by Chinese-speaking threat…