Category: GBHackers
The cybersecurity landscape has been disrupted by the emergence of Lucid, a sophisticated Phishing-as-a-Service (PhAAS) platform developed by Chinese-speaking threat…
Cybersecurity threats continue to evolve, with malicious actors exploiting popular platforms like Google Ads to spread malware. Recently, a sophisticated…
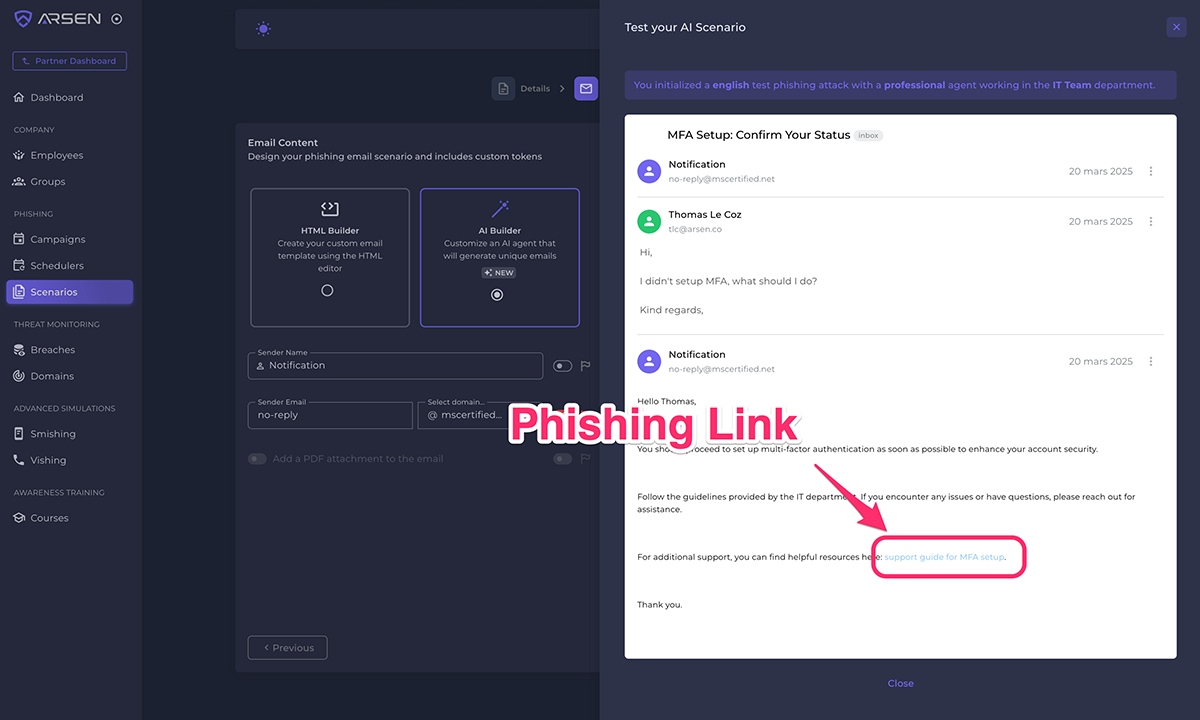
Paris, France, March 24th, 2025, CyberNewsWire Arsen, a leading cybersecurity company specializing in social engineering defense, today announced the full…
VanHelsingRaaS, a newly launched ransomware-as-a-service (RaaS) program, has quickly gained traction in the cybercrime ecosystem. Introduced on March 7, 2025,…
The Federal Communications Commission (FCC) has initiated a new investigation into Chinese entities previously identified as national security risks to…
CleanStack is a novel stack protection mechanism designed to combat memory corruption attacks, which have long been a significant threat…
An INTERPOL-led operation, dubbed “Operation Red Card,” has resulted in the arrest of over 306 individuals suspected of involvement in…
A recent cyber espionage operation by a China-nexus threat actor, dubbed “Weaver Ant,” has been uncovered by Sygnia, a cybersecurity…
A critical vulnerability in the popular WordPress plugin GamiPress has been uncovered, leaving users exposed to unauthenticated SQL injection attacks….
Google has recently rolled out a critical security update for its Chrome browser, addressing vulnerabilities that could potentially allow attackers…
A new strain of malware, known as SvcStealer, has emerged as a significant threat in the cybersecurity landscape. This malware…
North Korea has taken a significant step in enhancing its cyber warfare capabilities by establishing a new research center, known…