Category: GBHackers
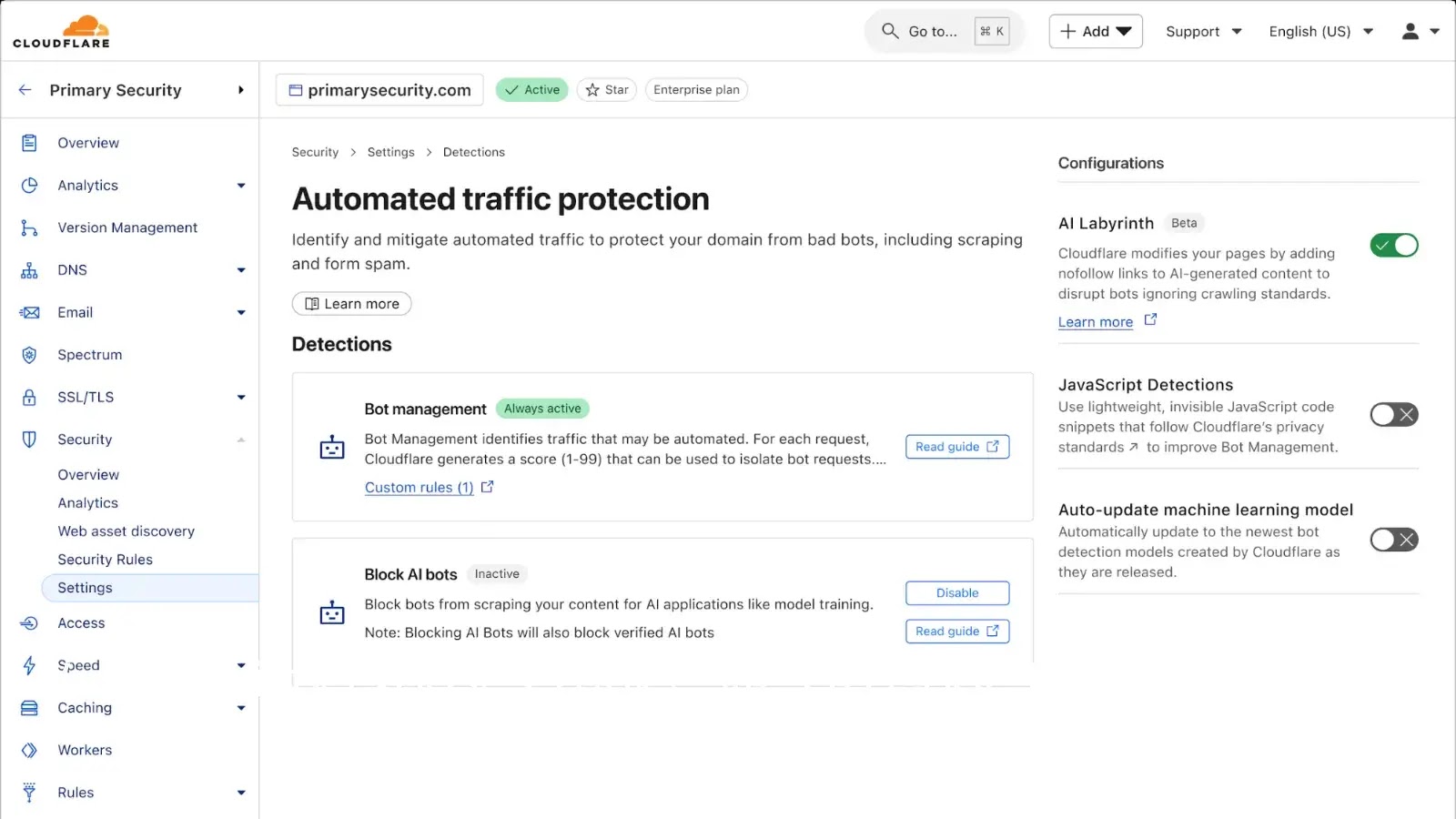
Cloudflare has unveiled AI Labyrinth, an innovative platform designed to combat AI-powered bots that relentlessly crawl and scrape data from websites…
A critical security vulnerability has been discovered in the popular WordPress plugin, WP Ghost, which boasts over 200,000 active installations….
A severe vulnerability has been identified in Next.js, a popular React framework used for building web applications, under the designation…
Chinese tech giant Baidu has faced severe scrutiny after allegations emerged that a top executive’s teenage daughter had accessed and…
Cloudflare has introduced a groundbreaking browser-based Remote Desktop Protocol (RDP) solution. This innovative tool allows users to securely access Windows…
In a recent surge of cyber threats, threat actors have been exploiting Reddit to distribute two potent malware variants: AMOS…
A recent phishing campaign uncovered by the Cofense Phishing Defense Center (PDC) has been exploiting fake Meta emails to deceive…
JumpServer, a widely used open-source Privileged Access Management (PAM) tool developed by Fit2Cloud, has been found to have critical security…
A recent article by Noah Gregory has highlighted a significant vulnerability in macOS, identified as CVE-2024-54471, which was patched in…
Researchers have recently discovered a sophisticated Python-based backdoor, known as the Anubis Backdoor, deployed by the notorious cybercrime group FIN7….
In a recent surge of sophisticated cyberattacks, threat actors have been utilizing fake CAPTCHA challenges to trick users into executing…
Recent research by Trend Micro has uncovered a significant evolution in the Albabat ransomware, which now targets not only Windows…