Category: GBHackers
In a stark revelation of the escalating cyber threat landscape, Flashpoint’s latest intelligence report highlights the alarming rise in compromised…
Threat actors have recently been exploiting legacy drivers to bypass certificate validation, leveraging a technique known as “Legacy Driver Exploitation.”…
Threat actors have increasingly been leveraging legitimate remote monitoring and management (RMM) software to infiltrate and navigate through networks undetected….
In a significant discovery, PRODAFT’s security research team has identified two critical vulnerabilities in the mySCADA myPRO Manager, a widely…
A newly identified cybersecurity threat involves attackers embedding malicious Word files within PDFs to deceive detection systems. This technique, confirmed…
The average corporate user now has 146 stolen records linked to their identity, an average 12x increase from previous estimates,…
Supervisory Control and Data Acquisition (SCADA) systems play a pivotal role in managing critical infrastructure across sectors like energy, manufacturing,…
Recently, several critical vulnerabilities were discovered in Sante PACS Server version 4.1.0, leaving it susceptible to severe security breaches. These…
A threat intelligence researcher from Cato CTRL, part of Cato Networks, has successfully exploited a vulnerability in three leading generative…
California Cryobank, a leading sperm donation facility based in Los Angeles, has been impacted by a significant data breach, potentially…
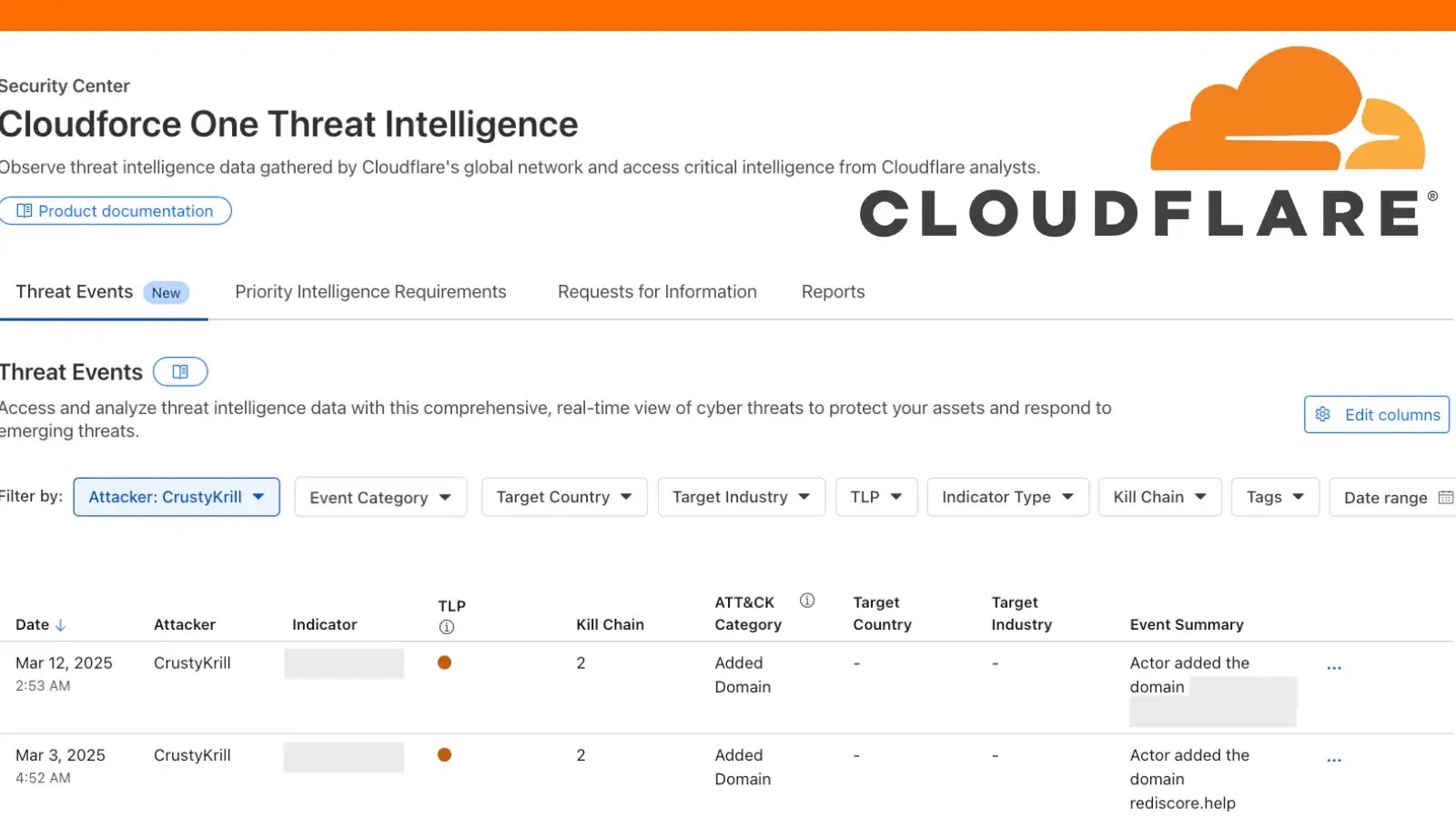
Cloudflare, a leading web infrastructure and security company, has launched the Cloudforce One threat events platform, designed to revolutionize how…
A recent cybersecurity incident has highlighted the sophisticated methods used by hackers to target web applications, particularly in South Korea….