Category: GBHackers
GitLab announced the release of versions 17.9.2, 17.8.5, and 17.7.7 for both its Community Edition (CE) and Enterprise Edition (EE)….
Free Webinar – Supply Chain Attack Prevention Recent attacks like Polyfill[.]io show how compromised third-party components become backdoors for hackers….
The United States has taken significant steps to address the growing threat of Chinese cyber intrusions into U.S. government agencies…
CYREBRO, the AI-native Managed Detection and Response (MDR) solution, announced today that it won Silver in the category of Security…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an advisory regarding a significant vulnerability in the Microsoft Windows…
The cybersecurity landscape witnessed a significant development when the National Police Agency (NPA) and the National center of Incident readiness…
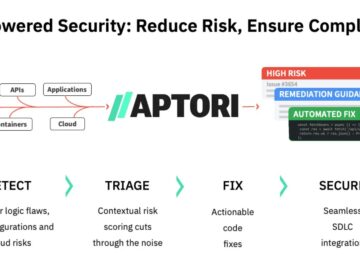
Aptori’s AI-Driven AppSec Platform Proactively Eliminates Vulnerabilities to Minimize Risk and Ensure Compliance. Aptori, a leader in AI-driven application security,…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical warning regarding a recently discovered vulnerability in Microsoft’s Windows…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning regarding a critical vulnerability in the Microsoft Windows Fast…
The Cybersecurity and Infrastructure Security Agency (CISA) highlighted a critical vulnerability affecting the Microsoft Windows Win32 kernel subsystem. Identified as…
Microsoft has rolled out its March 2025 Patch Tuesday update, addressing a total of 57 vulnerabilities across its software ecosystem,…
In recent years, phishing has remained the most prevalent form of cyberattack, with approximately 1.2% of global email traffic being…