Category: GBHackers
A new variant of malware, dubbed “Poco RAT,” has emerged as a potent espionage tool in a campaign targeting Spanish-speaking…
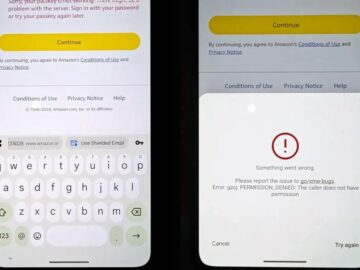
Google is rolling out a new privacy-focused feature called Shielded Email, designed to prevent apps and services from accessing users’ primary…
Unit 42 researchers have observed a threat actor group known as JavaGhost exploiting misconfigurations in Amazon Web Services (AWS) environments…
Cybersecurity experts are warning of an increasing trend in fileless attacks, where hackers leverage PowerShell and legitimate Microsoft applications to…
At the upcoming Black Hat Asia 2025 conference, cybersecurity experts will unveil a groundbreaking vulnerability in modern dashcam technology, exposing…
Hacktivism, once synonymous with symbolic website defacements and distributed denial-of-service (DDoS) attacks, has evolved into a sophisticated tool for cyber…
Belgium’s State Security Service (VSSE) has suffered what is being described as its most severe security breach to date. For…
Multi-factor authentication (MFA), long considered a cornerstone of cybersecurity defense, is facing a formidable new threat: “Pass-the-Cookie” attacks. Recent findings reveal…
A critical security flaw (CVE-2025-20059) has been identified in supported versions of Ping Identity’s PingAM Java Agent, potentially enabling attackers…
A sophisticated cyberespionage campaign linked to Chinese state-sponsored actors has exploited a previously patched Check Point VPN vulnerability (CVE-2024-24919) to…
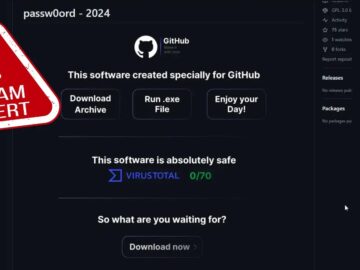
A sophisticated malware campaign leveraging GitHub repositories disguised as game modifications and cracked software has been uncovered, exposing a dangerous…
A sweeping analysis of the Common Crawl dataset—a cornerstone of training data for large language models (LLMs) like DeepSeek—has uncovered…