Category: GBHackers
Cybercriminals are increasingly leveraging sophisticated Adversary-in-the-Middle (AiTM) phishing techniques, enabled by the rise of Phishing-as-a-Service (PhaaS) ecosystems. These operations target…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released seven Industrial Control Systems (ICS) advisories on February 20, 2025, addressing…
The once-shadowy realm of Pegasus spyware has breached new frontiers, with forensic analyses revealing a stark pivot from targeting journalists…
Cybersecurity researchers have uncovered a sophisticated malware campaign orchestrated by the threat actor group SmartApeSG, also known as ZPHP or…
A recent phishing campaign conducted by cybersecurity firm Hackmosphere has revealed alarming vulnerabilities among top decision-makers, including CEOs and CTOs….
Security researchers have uncovered a significant evolution in the ShadowPad malware family, which is now being used to deploy ransomware…
Cybersecurity experts have raised alarms about the Rhadamanthys Infostealer, a sophisticated malware now being distributed through Microsoft Management Console (MMC)…
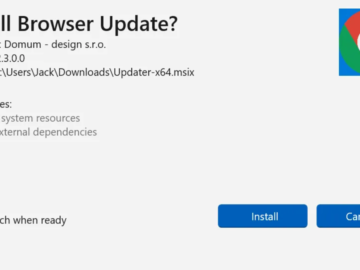
A recent investigation has uncovered a malicious application, DriverEasy, masquerading as a legitimate Google Chrome update to steal user credentials….
Cybersecurity researchers from Palo Alto Networks’ Unit 42 disclosed the resurgence of the Bookworm malware, which has been linked to…
As of February 2025, ransomware remains a formidable cyber threat, evolving in complexity and scale. The ransomware ecosystem has adapted…
A recent investigation into Ivanti Endpoint Manager (EPM) has uncovered four critical vulnerabilities that could allow unauthenticated attackers to exploit…
Check Point Software Technologies Ltd. has announced plans to establish its inaugural Asia-Pacific Research and Development (R&D) Centre in Bengaluru,…