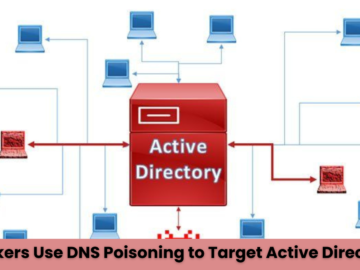
Category: GBHackers
Doppler, the leading provider of secrets management solutions, announced a new integration with Datadog, a cloud application monitoring and security…
A recent investigation by Unit 42 of Palo Alto Networks has uncovered a sophisticated, state-sponsored cyberespionage operation, tracked as CL-STA-0048….
Proofpoint researchers have identified a marked increase in phishing campaigns and malicious domain registrations designed to exploit tax filing season….
The cybersecurity landscape faces increasing challenges as Arcus Media ransomware emerges as a highly sophisticated threat. This Ransomware-as-a-Service (RaaS) operation,…
Since mid-2024, cybersecurity researchers have been monitoring a sophisticated Android malware campaign dubbed “Tria Stealer,” which exploits fake wedding invitations…
A groundbreaking technique for Kerberos relaying over HTTP, leveraging multicast poisoning, has been recently detailed by cybersecurity researchers. Introduced by…
Proton, the globally recognized provider of privacy-focused services such as Proton VPN and Proton Pass, is facing scrutiny after the…
Over 10,000 WordPress websites have been hijacked to deliver malicious software targeting both macOS and Windows users. Researchers revealed this…
In a critical development within the AI industry, researchers at Noma Security have disclosed the discovery of a high-severity Remote…
Cybersecurity researchers have identified a persistent trend in which threat actors exploit vulnerabilities in government websites to further phishing campaigns….
A new wave of cybercrime is surfacing as hackers exploit compromised emails and digital advertising platforms to create a thriving…
A recent investigation conducted by STRIKE, a division of SecurityScorecard, has unveiled the intricate and far-reaching operation of the Lazarus…