Category: GBHackers
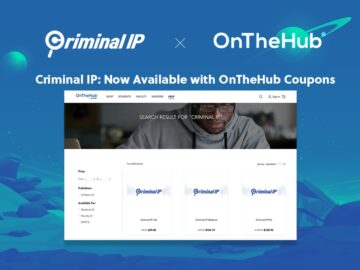
AI SPERA, a leading Cyber Threat Intelligence (CTI) provider, has collaborated with OnTheHub, a global provider of software in education,…
The Cybersecurity and Infrastructure Security Agency (CISA) announced three new Industrial Control Systems (ICS) advisories. These advisories provide critical insights…
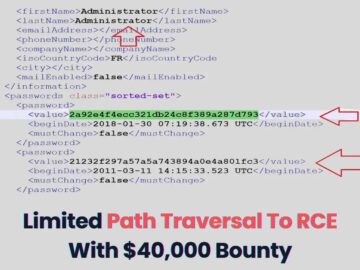
Cybersecurity researchers Abdullah Nawaf and Orwa Atyat, successfully escalated a limited path traversal vulnerability into a full-blown remote code execution…
A potential security flaw in IBM i Access Client Solutions (ACS) has raised serious concerns about password leakage, leaving users…
A ransomware attack has compelled UK Brit, a prominent British high school, to close its doors to students for two…
A security researcher, exploring reverse engineering and exploit development, has successfully identified a critical vulnerability in the TP-Link TL-WR940N router,…
The Open Web Application Security Project (OWASP) has released its updated Smart Contract Top 10 for 2025, providing essential insights for developers…
In early January 2025, a new ransomware strain identified as Contacto surfaced, showcasing advanced techniques designed to bypass conventional security…
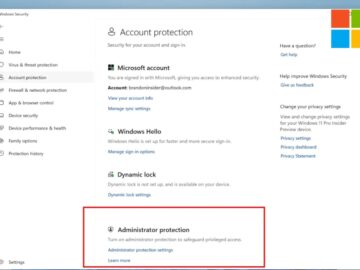
Microsoft has announced the release of Windows 11 Insider Preview Build 27774 to the Canary Channel. This build comes packed…
Colm O hEigeartaigh announced a critical vulnerability affecting various versions of Apache CXF, a widely-used framework for building web services….
A significant security vulnerability, designated CVE-2025-21613, has been discovered in the go-git library, used for Git version control in pure…
The Gootloader malware family employs sophisticated social engineering tactics to infiltrate computers. By leveraging compromised legitimate WordPress websites, Gootloader’s operators…