Category: GBHackers
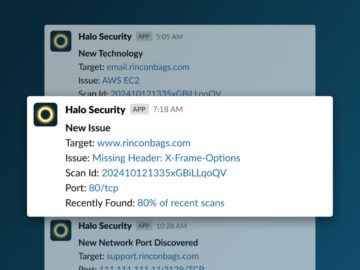
Halo Security, a leader in external attack surface management and penetration testing, has announced the launch of its new Slack®…
FrostyGoop, a newly discovered OT-centric malware that exploited Modbus TCP to disrupt critical infrastructure in Ukraine, capable of both internal…
Federal authorities have unsealed charges against five individuals accused of orchestrating sophisticated phishing schemes that targeted employees of companies across…
Helldown, a new ransomware group, actively exploits vulnerabilities to breach networks, as since August 2024, they have compromised 28 victims,…
A race condition vulnerability in Apple’s WorkflowKit has been identified, allowing malicious applications to intercept and manipulate shortcuts on macOS…
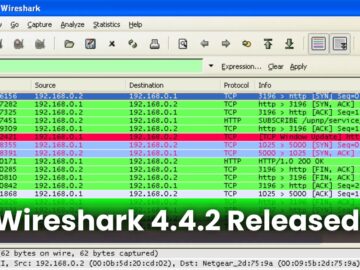
The Wireshark Foundation has officially announced the release of Wireshark 4.4.2, the latest version of the world’s most popular network…
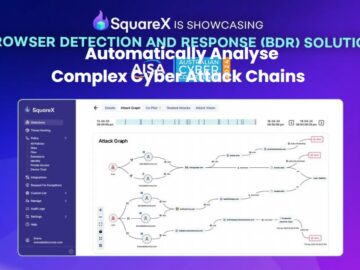
SquareX, the leading browser security company, will make its Australian debut at Melbourne CyberCon 2024, hosted by AISA (Australian Information…
North Korean IT workers, operating under the cluster CL-STA-0237, have been implicated in recent phishing attacks leveraging malware-infected video conference…
Water Barghest, a sophisticated botnet, exploits vulnerabilities in IoT devices to enlist them in a residential proxy marketplace by leveraging…
APT31, using the Rekoobe backdoor, has been observed targeting TradingView, a popular financial platform, as researchers discovered malicious domains mimicking…
Sonatype, the company behind the popular Nexus Repository Manager, has issued security advisories addressing two critical vulnerabilities affecting Nexus Repository…
Cybersecurity researchers have detected the active exploitation of a zero-day vulnerability in GeoVision devices, which the manufacturer no longer supports….