Category: GBHackers
FreeBSD has disclosed a critical remote code execution (RCE) vulnerability affecting its bhyve hypervisor. This vulnerability, CVE-2024-41721, could allow attackers…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued six advisories concerning vulnerabilities: Rockwell Automation’s RSLogix 5 and RSLogix 500…
GitLab has issued an urgent call to action for organizations using its platform to patch a critical authentication bypass vulnerability….
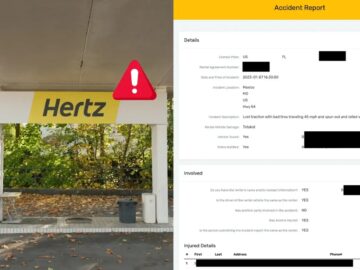
Hertz, a well-known car rental company, has inadvertently exposed over 60,000 insurance claim reports. This breach has raised serious concerns…
Recent intelligence indicates a new technique employed by stealers to trick victims into entering credentials directly into a browser, enabling…
Researchers identified an attack campaign targeting poorly secured Linux SSH servers, where the attack leverages Supershell, a cross-platform reverse shell…
Researchers discovered a large, Chinese state-sponsored IoT botnet, “Raptor Train,” that compromised over 200,000 SOHO and IoT devices. Operated by…
SambaSpy Attacking Windows Users With Weaponized PDF FilesResearchers discovered a targeted cybercrime campaign in May 2024 that exclusively focused on…
The anonymity of the Tor network has been scrutinized in a recent investigation by German law enforcement agencies. Despite these…
A threat actor has allegedly put up for sale a database belonging to Bharat Petroleum Corporation Limited (BPCL). This alarming…
The Chrome team has officially announced the release of Chrome 129, which is now available on the stable channel for…
VMware has issued a critical security advisory (VMSA-2024-0019) addressing two significant vulnerabilities in its vCenter Server and VMware Cloud Foundation…