Category: GBHackers
Researchers analyzed a malicious Android sample created using Spynote RAT, targeting high-value assets in Southern Asia, which, likely deployed by…
Dell Technologies has issued a security advisory, DSA-2024-439, to alert users of a critical vulnerability in its Dell Power Manager…
The Apache ActiveMQ server is vulnerable to remote code execution (CVE-2023-46604), where attackers can exploit this vulnerability by manipulating serialized…
Cybersecurity researchers have unveiled an advanced technique to uncover hackers’ operational infrastructure using passive DNS data. This groundbreaking method sheds…
A sophisticated crypto-stealing malware, Realst, has been targeting Web3 professionals, as the threat actors behind this campaign have employed AI-generated…
Let’s Encrypt has officially announced its timeline to phase out support for the Online Certificate Status Protocol (OCSP). The nonprofit…
Cybercriminals online take advantage of well-known events to register malicious domains with keywords related to the event, with the intention…
An international cybercrime network responsible for stealing millions of euros across at least ten European countries has been dismantled in…
Gamaredon, a persistent threat actor since 2013, targets the government, defense, diplomacy, and media sectors of their victims, primarily through…
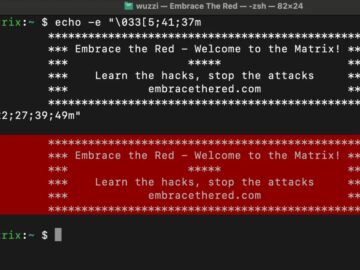
Researchers have uncovered that Large Language Models (LLMs) can generate and manipulate ANSI escape codes, potentially creating new security vulnerabilities…
Google has officially launched Vanir, an open-source security patch validation tool designed to streamline and automate the process of ensuring software…
Raspberry Pi, a pioneer in affordable and programmable computing, has once again elevated its game with the launch of the Raspberry…