Category: GBHackers
In modern business, cybersecurity is not merely a technical concern but a crucial financial safeguard. With cyber threats growing in…
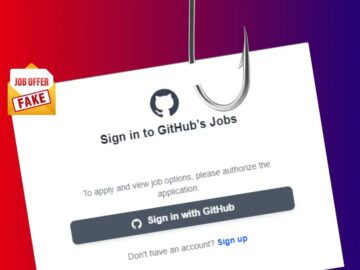
A new phishing campaign is targeting developers by exploiting GitHub’s legitimate infrastructure. This sophisticated attack involves fake job offers sent…
The Researcher team has identified and patched a critical privilege escalation vulnerability in the LiteSpeed Cache plugin. This plugin, installed…
Researchers analyze the security of MIFARE Classic cards, focusing exclusively on card-only attacks. They uncover multiple new attack vectors by…
RipperSec, a pro-Palestinian, pro-Muslim Malaysian hacktivist group, has rapidly grown since its Telegram inception in June 2023. Leveraging a community…
Raspberry Pi has announced the launch of a new 2GB variant of the Raspberry Pi 5, priced at an affordable…
A critical vulnerability has been discovered in the GiveWP plugin, a popular WordPress donation and fundraising platform. This vulnerability, CVE-2024-5932,…
Autodesk has disclosed a critical vulnerability in its AutoCAD software, which could allow malicious actors to execute arbitrary code. This…
AI SPERA, a leading Cyber Threat Intelligence (CTI) company, has announced a strategic partnership with Hackers Central, a major cybersecurity…
The notorious Lazarus hacker group has been identified as exploiting a zero-day vulnerability in Microsoft Windows, specifically targeting the Windows…
Researchers have uncovered a critical vulnerability within the Linux kernel’s dmam_free_coherent() function. This flaw, identified as CVE-2024-43856, stems from a race condition…
Researchers from the University of Rochester have unveiled a novel technique to defend against cache side-channel attacks, a prevalent threat…