Category: GBHackers
The Apache HTTP Server relies on hundreds of independently developed modules to handle client requests, sharing a complex data structure…
Threat actors often target and exploit security flaws in web browsers, as exploiting flaws in web browsers enables them to…
A sophisticated phishing campaign targeting Windows systems leverages multiple evasion techniques, including Python obfuscation, shellcode generation, and loading, to deploy…
Ransomware affiliates are forming alliances to recoup losses from unreliable partners. A prominent example involves ALPHV extorting $22 million from…
Authorities have dismantled a “laptop farm” in Nashville, Tennessee, allegedly used to support the Democratic People’s Republic of Korea’s (DPRK)…
A sophisticated threat activity cluster, STAC6451, has been identified targeting Microsoft SQL servers. This cluster, primarily observed by Sophos Managed…
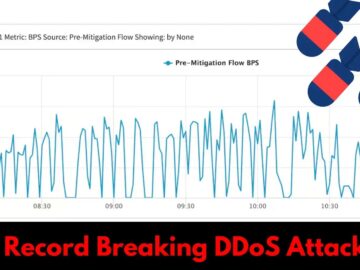
A record-breaking Distributed Denial of Service (DDoS) attack unleashed 419 terabytes of malicious traffic over 24 hours. This unprecedented event,…
Cisco has issued a security advisory warning users of its Small Business SPA300 and SPA500 Series IP Phones about multiple…
The Tor Project has announced the release of Tor Browser 13.5.2, now available for download from the Tor Browser download…
Amazon’s e-commerce platforms and cloud services form a digital ecosystem requiring a strong cybersecurity framework. Amazon, which has a vast…
Deep learning models analyzing API sequences for Windows malware detection face challenges due to evolving malware variants. A group of…
A vulnerability in Microsoft 365 (formerly Office 365) has been found that allows malicious actors to bypass anti-phishing measures. One…