Category: GBHackers
A critical local privilege escalation vulnerability has been discovered in RaspAP, an open-source project designed to transform Raspberry Pi devices…
Onyx Sleet, a cyber espionage group also known as SILENT CHOLLIMA, Andariel, DarkSeoul, Stonefly, and TDrop2, mainly targets the military,…
A malicious campaign emerged on June 21, 2024, distributing a JavaScript file hosted on grupotefex.com, which executes an MSI installer,…
Hackers continuously exploit malicious Python packages to attack developer environments and inject harmful code that enables them to steal sensitive…
Hackers often attack secure boot during the boot process to execute unauthorized code, which gives them the ability to bypass…
The French government has investigated a malware attack that compromised approximately 3,000 machines within the country. The attack, part of…
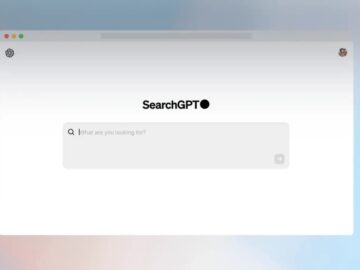
San Francisco, CA – OpenAI has announced the launch of SearchGPT, a groundbreaking prototype designed to revolutionize how users search…
Play Ransomware and LockBit Ransomware have reportedly allied to enhance their capabilities in launching cyber attacks. This collaboration, which involves…
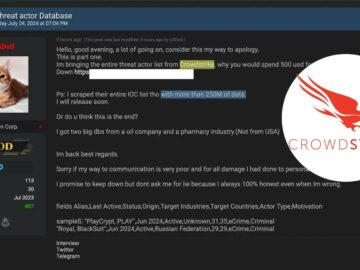
A hacktivist entity known as USDoD has asserted that it has leaked CrowdStrike’s “entire threat actor list” and claims to…
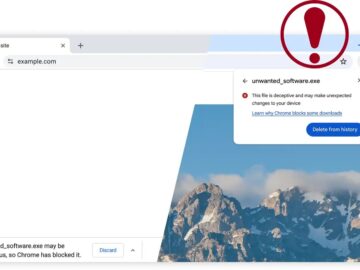
Google Chrome has introduced a revamped download experience with comprehensive warnings about potentially malicious files. This update is part of…
Researchers have uncovered a vulnerability in Microsoft’s Windows Hello for Business (WHfB) that allows attackers to bypass its robust authentication…
Cybersecurity experts have uncovered a sophisticated variant of the LummaC2 malware that leverages the popular Steam gaming platform as a…