Category: GBHackers
Chainalysis has launched Operation Spincaster, an initiative to disrupt approval phishing scams that have drained billions from victims’ wallets. This…
Meeting apps are often targeted and turned into weapons by hackers as they are largely employed for communication and collaboration,…
Hackers exploit open-source tools to execute attacks because they are readily available, well-documented, and often have extensive community support, making…
Threat actors often attack VMware ESXi servers since they accommodate many virtual machines, which link to a variety of systems…
Since October 2023, MuddyWater, which is an Iranian threat group linked to MOIS, has escalated its phishing campaigns in Middle…
HTTP Request Smuggling is a flaw in web security that is derived from variations in the way different web servers…
Researchers at Bitdefender Labs remain ever-vigilant, informing users about the latest scams and internet perils that threaten their security and…
The Volcano Demon group has been discovered spreading a new ransomware called LukaLocker, which targets Idealease Inc., a truck leasing…
Quick take: Harmony is the fourth cybersecurity application Resonance developed to address the disconnect in cybersecurity practices. Harmony captures continuous…
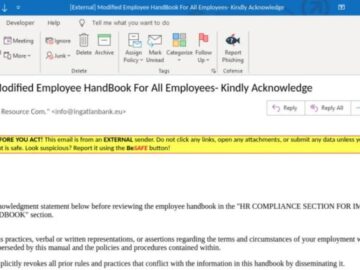
Phishing attacks are becoming increasingly sophisticated, and the latest strategy targeting employees highlights this evolution. This new phishing attempt impersonates…
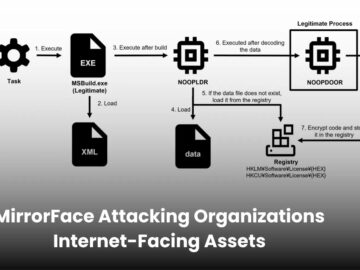
MirrorFace threat actors have been targeting media, political organizations, and academic institutions since 2022, shifting focus to manufacturers and research…
In 2022, HardBit Ransomware emerged as version 4.0. Unlike typical ransomware groups, this ransomware doesn’t use leak sites or double…