Category: GBHackers
In 2022, HardBit Ransomware emerged as version 4.0. Unlike typical ransomware groups, this ransomware doesn’t use leak sites or double…
The hackers weaponize 7zip files to pass through security measures and deliver malware effectively. These archived files can hide malicious…
X-Labs identified basic ransomware targeting Turkish businesses, delivered via PDF attachments in suspicious emails from the internet[.]ru domain. PDF links…
Cyble Research & Intelligence Labs (CRIL) researchers have identified a cyber threat targeting the upcoming Paris Olympics. On June 23,…
EBooks are popular, and their popularity lucrative threat actors the most, as they are widely shared digital assets that can…
A critical vulnerability has been discovered in the Cellopoint Secure Email Gateway, identified as CVE-2024-6744. This flaw assigned a CVSS…
Airlines often become the target of hackers as they contain sensitive personal and financial details of passengers as well as…
ViperSoftX is an advanced malware that has become more complicated since its recognition in 2020, to the extent that eBooks…
A Houthi-aligned group has been deploying Android surveillanceware called GuardZoo since October 2019 to target military personnel in the Middle…
The Monetary Authority of Singapore (MAS) and The Association of Banks in Singapore (ABS) announced today that major retail banks…
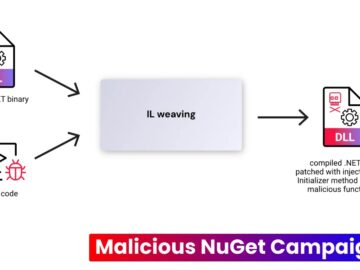
Hackers often target NuGet as it’s a popular package manager for .NET, which developers widely use to share and consume…
DarkGate, a Malware-as-a-Service (MaaS) platform, experienced a surge in activity since September 2023, employing various distribution methods, including email attachments,…