Category: GBHackers
Roblox, the globally renowned online gaming platform, has suffered a data breach. According to a tweet from cybersecurity expert H4ckManac,…
A Technically Skilled individual who finds a bug faces an ethical decision: report the bug or profit from it. This…
Kimsuky, also known as the Velvet Chollima, Black Banshee, THALLIUM, or Emerald Sleet, is a North Korean state-sponsored advanced cyber…
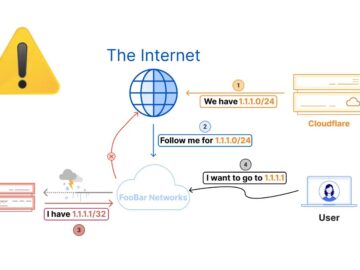
On June 27, 2024, Cloudflare experienced a disruption of its 1.1.1.1 DNS resolver service. This several-hour incident was caused by…
Active since 2015, Mekotio is a Latin American banking trojan specifically designed to target financial data in regions like Brazil,…
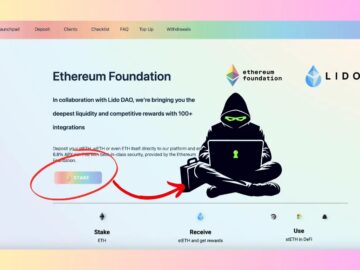
In a recent cyberattack, hackers successfully compromised Ethereum’s mailing list, attempting to drain users’ crypto funds through a sophisticated phishing…
An unauthenticated endpoint vulnerability allowed threat actors to identify phone numbers associated with Authy accounts, which was identified, and the…
Over 380,000 web hosts have been found embedding a compromised Polyfill.io JavaScript script, linking to a malicious domain. This supply…
Hackers target and weaponize AnyDesk, Zoom, Teams, and Chrome as these applications are widely used in a multitude of sectors….
A new player has emerged on the cybercrime landscape the ransomware group “Pryx.” Pryx has claimed its first attack, announcing…
Hiap Seng Industries, a prominent engineering and construction company, has fallen victim to a ransomware attack that compromised its servers….
Gogs is a standard open-source code hosting system used by many developers. Several Gogs vulnerabilities have been discovered recently by…