Category: GBHackers
TotalEnergies Clientes SAU has reported a significant cyberattack that has compromised the personal data of 210,715 customers. The incident has…
A vulnerability in Junos OS on SRX Series devices allows attackers to trigger a DoS attack by sending crafted valid…
The Rafel RAT is an advanced Android-targeting Remote Access Trojan which poses a great cybersecurity danger. This malicious program has…
Cisco has disclosed a critical vulnerability in its widely-used NX-OS network operating system that could allow attackers to execute arbitrary…
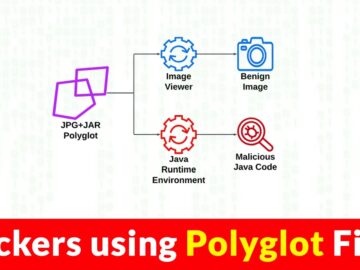
Polyglot files have to fit in several file format specifications and respond differently depending on the calling program. This poses…
Google has unveiled kvmCTF, a new vulnerability reward program (VRP) explicitly targeting the Kernel-based Virtual Machine (KVM) hypervisor. This initiative,…
Hackers often mimic penetration testing services to disguise their malicious activities as legitimate security assessments. By imitating authorized security testing,…
A new Orcinius Trojan has been discovered, employing VBA Stomping to hide its infection. The multi-stage trojan uses Dropbox and…
Transparent Tribe (aka APT36) has been active since 2016, focusing on social engineering strategies to target Indian government and military…
Water Sigbin (8220 Gang) exploits vulnerabilities (CVE-2017-3506, CVE-2023-21839) in Oracle WebLogic servers to deliver cryptocurrency miners using PowerShell scripts. They…
Rapid7, Inc., a leader in extended risk and threat detection, has announced a definitive agreement to acquire Noetic Cyber, a…
The Qualys Threat Research Unit has identified a newly discovered vulnerability in OpenSSH, dubbed “regreSSHion” (CVE-2024-6387). This critical flaw, which…