Category: GBHackers
DuckDuckGo has unveiled a new feature, AI Chat, which offers users an anonymous way to access popular AI chatbots. This…
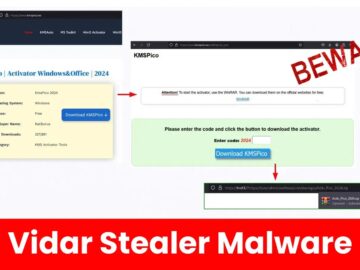
Researchers detected an attack involving a fake KMSPico activator tool, which delivered Vidar Stealer through several events. The attack leveraged…
Due to the growing popularity of Apple devices, cybercriminals are increasingly targeting iOS and macOS with malware. The App Store…
Sticky Werewolf, a cyber threat group, has shifted its targeting strategy from sending phishing emails with download links to malicious…
The North Korean state-sponsored group known as Kimsuky has launched a sophisticated cyber-espionage campaign targeting a prominent weapons manufacturer in…
Hacktivist groups are increasingly targeting critical infrastructure’s Operational Technology (OT) systems, motivated by geopolitical issues that, unlike traditional website defacements,…
Apache RocketMQ platform is a widely used messaging system that handles high volumes of data and critical operations, often attracting…
The government computer emergency response team of Ukraine, CERT-UA, in direct cooperation with the Cyber Security Center of the Armed…
ReversingLabs researchers recently uncovered a malicious open-source package named xFileSyncerx on the Python Package Index (PyPI). This package, which had…
Tenable® Holdings, Inc., a leading Exposure Management company, has announced a definitive agreement to acquire Eureka Security, Inc., a prominent…
It is difficult to secure cloud accounts from threat actors who exploit multi-factor authentication (MFA) settings. Threat actors usually alter…
A cybercriminal group is selling and distributing a sophisticated phishing kit called “V3B” through Phishing-as-a-Service (PhaaS) and self-hosting methods, which…