Category: GBHackers
Patelco Credit Union has disclosed a ransomware attack that compromised the personal data of its members and employees. The breach,…
Argentine authorities have arrested a Russian national accused of laundering cryptocurrency payments linked to the notorious North Korean Lazarus Group….
Dell Technologies has issued a critical security update for its Dell Power Manager software following the discovery of a significant…
The Progress WhatsUp Gold team confirmed the existence of critical vulnerabilities in all versions of their software released before 2024.0.0….
Google has announced the release of Chrome 128 to the stable channel for Windows, Mac, and Linux. This update, Chrome…
INE Security, a global cybersecurity training and certification provider, recently launched initiatives with several higher education institutions in an ongoing…
Cybersecurity researchers at Aqua Nautilus have uncovered a new malware named PG_MEM that targets PostgreSQL databases. This sophisticated malware employs…
Recent attacks exploit the Log4j vulnerability (Log4Shell) by sending obfuscated LDAP requests to trigger malicious script execution, which establishes persistence,…
In modern business, cybersecurity is not merely a technical concern but a crucial financial safeguard. With cyber threats growing in…
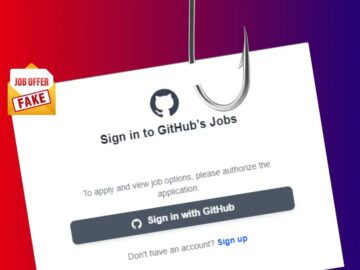
A new phishing campaign is targeting developers by exploiting GitHub’s legitimate infrastructure. This sophisticated attack involves fake job offers sent…
The Researcher team has identified and patched a critical privilege escalation vulnerability in the LiteSpeed Cache plugin. This plugin, installed…
Researchers analyze the security of MIFARE Classic cards, focusing exclusively on card-only attacks. They uncover multiple new attack vectors by…