Category: GBHackers
A critical vulnerability has been discovered in Spring Cloud Data Flow, a microservices-based platform for streaming and batch data processing…
Okta, a leading identity and access management company, has warned about credential stuffing attacks targeting its Customer Identity Cloud (CIC)….
In a shocking revelation, a threat actor has allegedly leaked sensitive data belonging to Shell, one of the world’s leading…
Researchers analyzed a batch of suspicious ELF files with low antivirus detection rates, which used anti-debugging techniques, obfuscation, and encryption,…
Phishing campaigns are abusing Cloudflare workers in two ways, where one injects malicious content hidden by HTML smuggling, similar to…
If there is a single theme circulating among Chief Information Security Officers (CISOs) right now, it is the question of…
Malicious traffic floods targeted systems, servers, or networks in Distributed Denial of Service (DDoS) attacks are actively exploited by hackers. …
Hackers target and exploit GitHub repositories for a multitude of reasons and illicit purposes. The widespread use of GitHub and…
Hackers employ DNS for various purposes like redirecting traffic to enable man-in-the-middle attacks, infecting malware through harmful sites, and flooding…
A new vulnerability has been discovered in macOS Sonoma that is associated with privilege escalation. This vulnerability has been assigned…
GNOME desktop manager was equipped with a new feature which allowed remote users to create graphical sessions on the system…
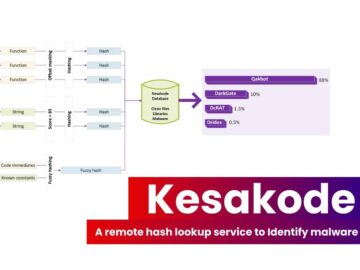
Today marks a significant milestone for Malcat users with the release of version 0.9.6, introducing Kesakode, a remote hash lookup…