Category: GBHackers
Tor Project has announced the release of Tor Browser 13.0.15. Available now on the Tor Browser download page and through…
Hackers exploit social engineering, which avoids technical security systems, by manipulating the psychology and behavior of a human being. Social…
In a concerning development for Dell Technologies, a threat actor known as Menelik has reportedly accessed and scraped sensitive customer…
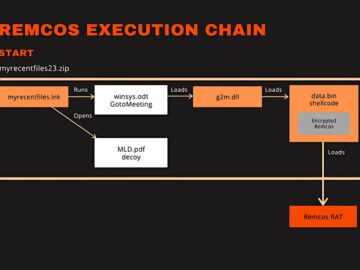
In a sophisticated cyberattack campaign, hackers are using the online meeting platform GoToMeeting to distribute a Remote Access Trojan known…
iTunes has been found to have an arbitrary code execution vulnerability that might allow attackers to execute malicious code. To…
The New Jersey Cybersecurity & Communications Integration Cell (NJCCIC) has detected a formidable new cyber threat. Dubbed LockBit Black, this…
As a sneaky scheme, hackers use DNS tunneling to bypass traditional security measures. By wrapping malicious data inside DNS queries…
In a recent development, Zscaler Inc., a prominent cybersecurity firm, has concluded its investigation into a potential data breach initially…
A notorious threat actor has decided to sell the INC Ransomware code for an unbelievable $300,000. As a result of…
OpenAI, the top lab for researching artificial intelligence, just released GPT-4o, its newest advance in AI technology. In the field…
In collaboration with Red Balloon Security, Narf Industries, and Niyo Little Thunder Pearson (ONEGas, Inc.), MITER has unveiled EMB3D, a…
Logicalis, the global technology service provider delivering next-generation digital managed services, has today announced the launch of Intelligent Security, a…