Category: GBHackers
Hackers often register new domains for phishing attacks, spreading malware, and other deceitful activities. Such domains are capable of pretending…
SonicWall has disclosed a critical heap-based buffer overflow vulnerability in its SonicOS IPSec VPN. This flaw, identified as CVE-2024-40764, can…
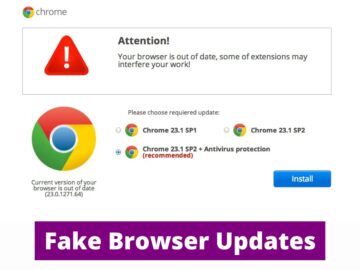
SocGholish malware, also known as FakeUpdates, has exhibited new behavior since July 4th, 2024, as the infection chain still begins…
UK police have arrested a 17-year-old boy from Walsall in connection with a notorious cyber hacking group. This group has…
A recent update from cybersecurity firm CrowdStrike has caused significant disruptions for Windows users, leading to widespread reports of Blue…
Chainalysis has launched Operation Spincaster, an initiative to disrupt approval phishing scams that have drained billions from victims’ wallets. This…
Meeting apps are often targeted and turned into weapons by hackers as they are largely employed for communication and collaboration,…
Hackers exploit open-source tools to execute attacks because they are readily available, well-documented, and often have extensive community support, making…
Threat actors often attack VMware ESXi servers since they accommodate many virtual machines, which link to a variety of systems…
Since October 2023, MuddyWater, which is an Iranian threat group linked to MOIS, has escalated its phishing campaigns in Middle…
HTTP Request Smuggling is a flaw in web security that is derived from variations in the way different web servers…
Researchers at Bitdefender Labs remain ever-vigilant, informing users about the latest scams and internet perils that threaten their security and…