Category: GBHackers
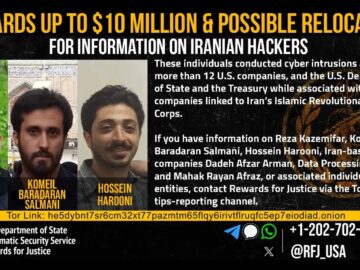
The United States Justice Department has announced big rewards for information leading to the capture of four Iranian nationals. These…
When cyber attacks strike, it’s rarely a single computer that suffers. Nowadays, cybercriminals set their sights on corporate networks, aiming…
Oracle Virtualbox was identified and reported as having a critical vulnerability associated with Privilege Escalation and Arbitrary File Move/Delete. This…
To combat the misuse of commercial spyware, the United States Department of State has announced visa restrictions on 13 individuals…
The Volkswagen Group has fallen victim to a sophisticated hacking incident, with over 19,000 sensitive documents stolen. Investigations point towards…
A significant vulnerability in the Perforce Akana Community Manager Developer Portal has been found, allowing attackers to conduct server-side request forgery…
A SIM Swap Scam or SIM Cloning Scam exploits a vulnerability in a two-factor authentication (2FA) system that relies on…
Security researchers have identified a critical vulnerability in Apache HugeGraph, an open-source graph database tool. This flaw, if exploited, could…
The ongoing tension between privacy rights and public safety, Europol, along with European Police Chiefs, has issued a call for…
A significant vulnerability has been identified in Citrix’s monitoring tool, uberAgent. If exploited, this flaw could allow attackers to escalate…
APT29, a Russian threat group, targeted German political parties with a new backdoor called WINELOADER using spear-phishing emails containing malicious…
Hackers often target PyPI packages to exploit vulnerabilities and inject malicious code into widely used Python libraries. Recently, cybersecurity researchers…