Category: GBHackers
In a groundbreaking move, the U.S. Department of Defense has released a comprehensive guide for organizations deploying and operating AI…
Cybersecurity researchers at Kaspersky have uncovered evidence that cybercriminal groups are customizing the virulent LockBit 3.0 ransomware for targeted attacks…
A new remote code execution vulnerability has been identified to be affecting multiple Microsoft products including .NET, .NET Framework and…
The revival of the LightSpy malware campaign has been observed, focusing on Indian Apple device users. This sophisticated mobile spyware,…
The Web3 movement is going from strength to strength with every day that passes. Slowly but surely, it’s building a…
A new malware known as LightSpy has been targeting Android and iOS users. This sophisticated surveillance tool raises alarms across…
In a recent security bulletin, Palo Alto Networks disclosed a critical vulnerability in its GlobalProtect Gateway, identified as CVE-2024-3400. This…
The software supply chain is filled with various challenges, such as untracked security vulnerabilities in open-source components and inconsistent update…
A LastPass employee recently became the target of an attempted fraud involving sophisticated audio deepfake technology. This incident underscores the…
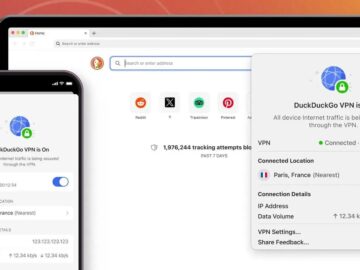
DuckDuckGo has launched Privacy Pro, a new subscription service that promises to enhance user privacy across the web. This innovative…
In response to a recent data breach at Sisense, a provider of data analytics services, the U.S. Cybersecurity and Infrastructure…
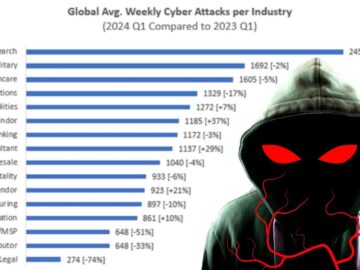
In Q1 2024, Check Point Research (CPR) witnessed a notable increase in the average number of cyber attacks per organization…