Category: GBHackers
Hackers exploit Oracle WebLogic Servers, knowing that they are extensively used in enterprises. Threat actors can use security vulnerabilities present…
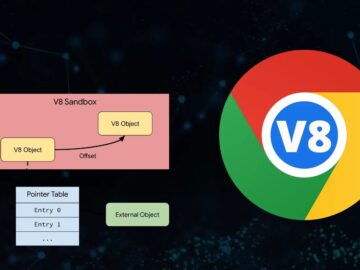
A Sandbox is a protective medium that blocks the entire system from any application accessing vulnerable resources. Restrictive environments for…
In a recent cybersecurity revelation, Ivanti, a leading provider of enterprise-grade secure access solutions, has been found to have significant…
Targus International, LLC and its affiliates fell victim to a sophisticated cyberattack. The company, an indirect subsidiary of B. Riley…
In a recent announcement, the team behind the widely acclaimed source code editor, Notepad++, has issued a call to arms…
Privacy mistakes could pose a serious threat to sensitive information or systems,, which threat actors could exploit for their gain….
Google has announced the global rollout of its revamped Find My Device network. This innovative feature is set to transform…
Researchers identified a significant vulnerability within the HTTP/2 protocol, potentially allowing hackers to launch Denial of Service (DOS) attacks on…
In the dynamic and ever-evolving landscape of cyber security defenses, enterprise-grade penetration testing is one of the most crucial practices…
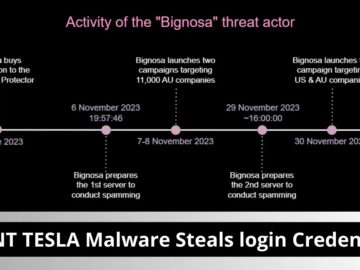
Researchers investigated a recent Agent Tesla malware campaign targeting US and Australian organizations, which used phishing emails with fake purchase…
Threat actors target home users with information-stealing malware like Vidar, StealC, and Lumma Stealer, which disguises the malware as pirated…
By exploiting the AI tools deepfake hackers could make videos or audios of political candidates to spread misinformation or disinformation,…