Category: GBHackers
The notorious WarzoneRAT malware has made a comeback, despite the FBI’s recent efforts to dismantle its operations. Initially detected in…
EclecticIQ cybersecurity researchers have uncovered a cyberespionage operation dubbed “Operation FlightNight” targeting Indian government entities and energy companies. The attackers,…
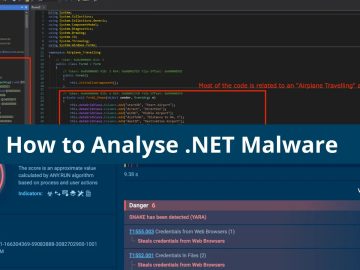
Utilizing sandbox analysis for behavioral, network, and process examination provides a foundation for reverse engineering .NET malware. The write-up outlines…
A comprehensive survey conducted by Keeper Security, in partnership with TrendCandy Research, has shed light on the growing concerns within…
GoPlus Labs, the leading Web3 security infrastructure provider, has unveiled a groundbreaking report highlighting the growing, widespread use and potential…
Zoom has taken a monumental leap forward by introducing Zoom Workplace, an all-encompassing AI-powered platform designed to redefine how we…
Wireshark stands as the undisputed leader, offering unparalleled tools for troubleshooting, analysis, development, and education. The latest update, Wireshark 4.2.4,…
Phishing allows hackers to exploit human vulnerabilities and trick users into revealing sensitive information and grant unauthorized access. It’s an…
Black Lotus Labs discovered a multi-year campaign by TheMoon malware targeting vulnerable routers and turning them into bots for the…
Google has announced a crucial update to its Chrome browser, addressing several vulnerabilities, including two zero-day exploits showcased at the…
Microsoft announced that Microsoft Edge WebView2 eligibility and specific out-of-scope information are now included in the Edge Bounty Program. The…
A critical vulnerability in Ray, an open-source AI framework that is widely utilized across various sectors, including education, cryptocurrency, and…