Category: GBHackers
To raise awareness of the ALPHV Blackcat ransomware as a service (RaaS) that targets the US healthcare industry, the FBI, CISA,…
Over the years, several reports associated with cybercriminals have been based in Russia and Western countries. This is due to…
Threat actors use weaponized PDF files for initial infection. This is because they can be embedded with malicious code, PDF…
In a significant cybersecurity incident, loanDepot, a prominent player in the loan and mortgage industry, announced a data breach that…
Cybersecurity experts have raised alarms over a new threat vector targeting Python developers: typo-squatting on the Python Package Index (PyPI)….
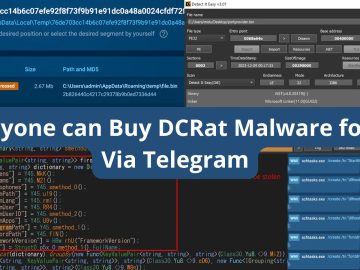
Researchers from ANY.RUN reported a new wave of DCRat malware, known for its wide array of harmful functions, selling the…
FortiGuard Labs has released a report detailing the emergence and impact of the Abyss Locker ransomware, which has been targeting…
The current large surge in cyber threats has left many organizations grappling for security so ThreatHunter.ai is taking decisive action….
ConnectWise, a prominent software company, issued an urgent security bulletin on February 19, 2024, revealing two significant vulnerabilities in its…
A critical security flaw has been identified in the Ultimate Member plugin for WordPress, which could potentially put over 200,000…
It has come to light that a group known as Anonymous Sudan is actively promoting a new Distributed Denial of…
Scattered Spider is a threat group responsible for attacking several organizations since May 2022 by using techniques like social engineering,…