Category: GBHackers
Threat actors on underground forums are now promoting a new “ClickFix” payload-delivery technique that hides malware in the browser cache…
Credit card fraud has matured into a service-based criminal economy where stolen cards, malware, and support are bundled and sold like commercial…
DigitStealer is an increasingly active macOS‑targeting infostealer whose predictable command‑and‑control (C2) setup exposes structural weaknesses in its operators’ infrastructure decisions….
Mozilla has released an emergency security update for Firefox, addressing a critical heap buffer overflow vulnerability in the libvpx library….
Attackers have weaponized a malicious fork of the legitimate Triton macOS client for omg.lol, turning a trusted open-source project into…
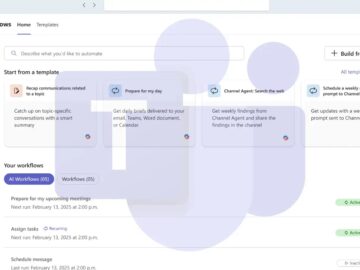
Microsoft is rolling out AI Workflows in the Teams Workflows app, bringing intelligent automation capabilities powered by Microsoft 365 Copilot…
Apache NiFi users are being urged to upgrade after the project disclosed a high-severity authorization flaw tracked as CVE-2026-25903. The…
A new ransomware-as-a-service (RaaS) outfit calling itself 0APT has quickly drawn attention for all the wrong reasons, after loudly claiming to have…
The Langchain development team has released a critical security update for the @langchain/community package to address a Server-Side Request Forgery (SSRF) vulnerability….
The three major cloud-based password managers, such as Bitwarden, LastPass, and Dashlane, collectively serve approximately 60 million users. Despite marketing…
A critical vulnerability in the popular CleanTalk Spam Protection plugin for WordPress exposes websites to complete takeover. Tracked as CVE-2026-1490,…
Joomla site owners using extensions that bundle the Novarain/Tassos Framework are being warned after a source code review identified multiple…