Category: GBHackers
Threat actors are increasingly abusing Discord webhooks as covert command-and-control (C2) channels inside open-source packages, enabling stealthy exfiltration of secrets,…
Security researchers have identified a new, active campaign of the Stealit malware that uses an experimental Node.js feature to infect…
Menlo Park, USA, October 10th, 2025, CyberNewsWire AccuKnox, a leader in Zero Trust Cloud Native Application Protection Platforms (CNAPP), is…
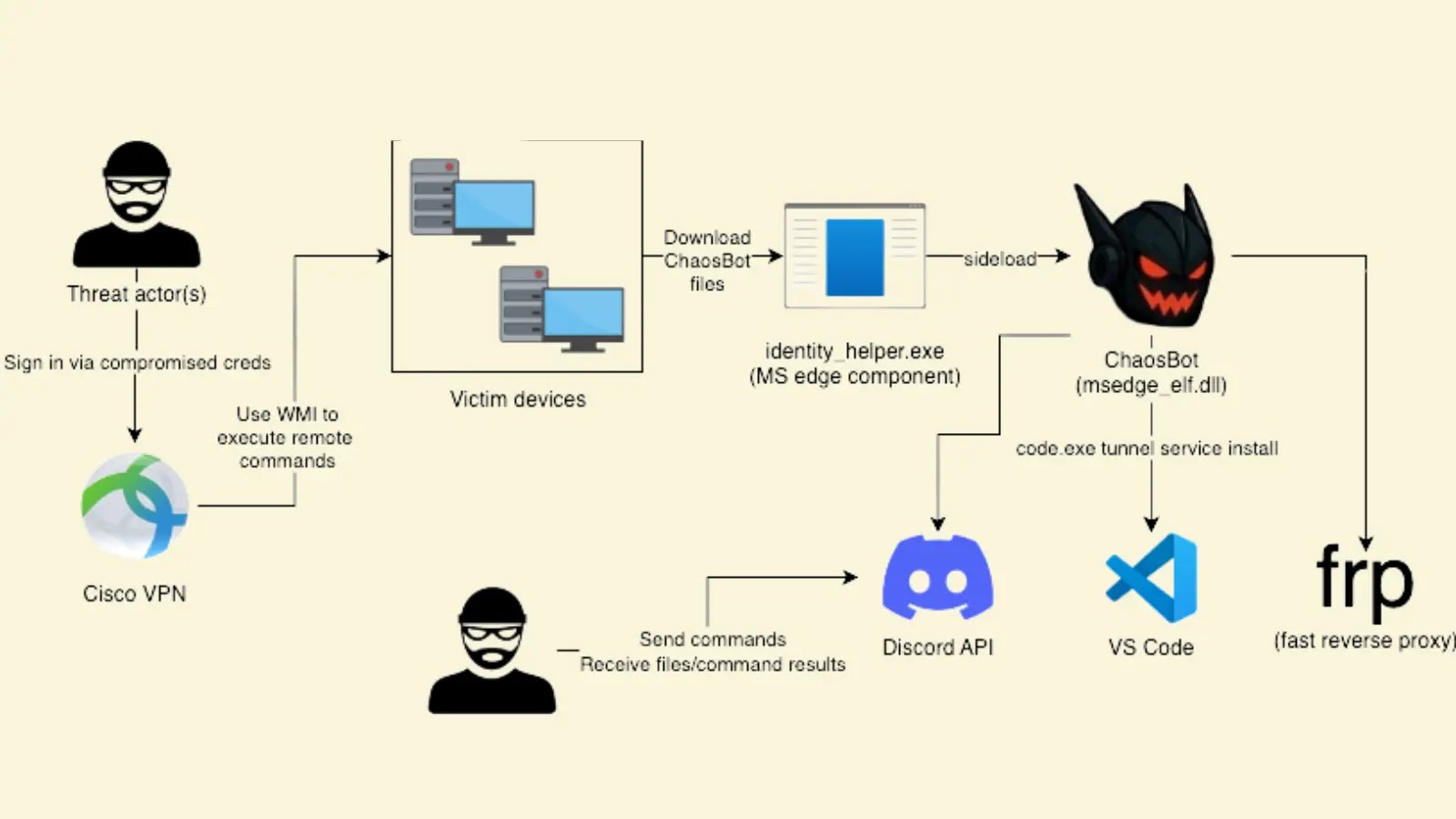
Adversaries have once again demonstrated that operational hours are irrelevant when mounting sophisticated cyberattacks. eSentire’s TRU team first observed suspicious…
A significant uptick in Akira ransomware attacks has been observed exploiting unpatched SonicWall SSL VPN devices between July and August…
Socket’s Threat Research Team has uncovered a sprawling phishing campaign—dubbed “Beamglea”—leveraging 175 malicious npm packages that have amassed over 26,000…
A critical weakness in GitHub Copilot Chat discovered in June 2025 exposed private source code and secrets to attackers. Rated…
LLM-enabled malware poses new challenges for detection and threat hunting as malicious logic can be generated at runtime rather than…
Gladinet CentreStack and Triofox have come under active attack as threat actors exploit an unauthenticated local file inclusion flaw (CVE-2025-11371)….
The RondoDox campaign’s “exploit shotgun” method leverages over 50 vulnerabilities across more than 30 vendors to infiltrate network devices, highlighting…
ClayRat, a rapidly evolving Android spyware campaign, has surged in activity over the past three months, with zLabs researchers observing…
A newly observed information‐stealing campaign is deploying a stealthy variant of the SnakeKeylogger malware via weaponized e-mails that masquerade as…