Category: GBHackers
Intel is pursuing legal action against a former software engineer who the company claims downloaded thousands of confidential files shortly…
Three critical vulnerabilities in runc, the widely-used container runtime that powers Docker and Kubernetes, have been disclosed, allowing attackers to…
Microsoft researchers have unveiled a sophisticated side-channel attack targeting remote language models that could allow adversaries to infer conversation topics…
Security researchers have discovered an actively exploited remote code execution vulnerability in Monsta FTP, a web-based FTP client used by…
A comprehensive new report reveals that manufacturing organizations are grappling with a dual challenge: rapidly adopting generative AI technologies while…
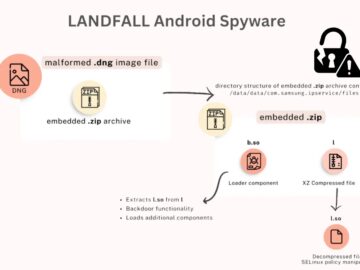
Cybersecurity researchers at Unit 42 have uncovered a sophisticated Android spyware campaign that exploited a previously unknown zero-day vulnerability in…
Microsoft is poised to roll out a significant update to Teams, enabling users to initiate chats with anyone using just…
Security researchers have uncovered a dangerous attack vector targeting Active Directory Sites, a critical yet often overlooked component of enterprise…
LockBit has remained one of the most dominant ransomware-as-a-service (RaaS) groups in the world since its emergence as ABCD ransomware…
ClickFix attacks have surged dramatically over the past year, cementing their position as pivotal tools in the modern attacker’s arsenal….
A new ransomware group, Cephalus, has emerged in the cybersecurity threat landscape, targeting organizations through compromised Remote Desktop Protocol (RDP)…
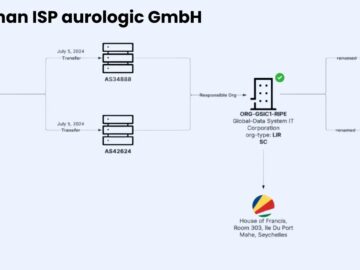
German hosting provider aurologic GmbH has emerged as a critical hub within the global malicious infrastructure ecosystem, according to recent…