Category: GBHackers
A new threat has surfaced in the mobile banking landscape Herodotus, a sophisticated Android banking Trojan that has been wreaking…
The Congressional Budget Office (CBO), which serves as Congress’s official financial advisor, has been targeted in a suspected cyberattack by…
Russian-based threat actors are actively distributing a sophisticated Android Remote Access Trojan called “Fantasy Hub” via Telegram-based Malware-as-a-Service channels, marking…
Cybersecurity researchers have uncovered a sophisticated phishing campaign that exploits compromised hotel booking accounts to defraud travellers worldwide. The campaign,…
Datadog Security Research has uncovered a sophisticated supply chain attack targeting the npm ecosystem, involving 17 malicious packages across 23…
Security researchers have developed a new technique that leverages call gadgets to insert arbitrary modules into the call stack during…
The OPNsense project has released version 25.7.7, delivering critical security improvements and performance enhancements to strengthen enterprise firewall deployments. This…
Chinese cyber-espionage groups have once again demonstrated their determination and technical prowess in targeting U.S. organizations with ties to international…
Security researchers have uncovered severe remote code execution vulnerabilities in three official Claude Desktop extensions developed and published by Anthropic….
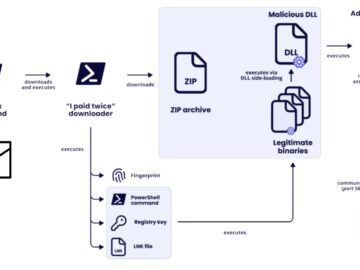
In July 2025, Doctor Web’s anti-virus laboratory received a critical alert from a government-owned organization within the Russian Federation. The…
Russia-aligned threat actor Sandworm has intensified its destructive cyber operations against Ukrainian organizations, deploying data wiper malware to cripple critical…
A recently disclosed vulnerability in the Amazon WorkSpaces client for Linux exposes a critical security flaw that could allow attackers…