Category: GBHackers
Russia-aligned threat actor Sandworm has intensified its destructive cyber operations against Ukrainian organizations, deploying data wiper malware to cripple critical…
A recently disclosed vulnerability in the Amazon WorkSpaces client for Linux exposes a critical security flaw that could allow attackers…
Security researchers have identified a sophisticated new malware family, Airstalk, that exploits VMware’s AirWatch API—now known as Workspace ONE Unified…
In the early hours of November 3, 2025, Check Point Research’s blockchain threat monitoring systems flagged a suspicious pattern on…
Cisco has issued a critical warning about ongoing attacks targeting a severe remote code execution vulnerability affecting its Secure Firewall,…
In the ever-evolving landscape of cyber threats, a new ransomware strain, Midnight, has emerged, echoing the notorious tactics of its…
A critical vulnerability discovered across numerous HTTP/2 implementations has exposed a dangerous protocol-level vulnerability that enables threat actors to orchestrate…
The emergence of AI-powered browsers represents a significant shift in how artificial intelligence interacts with web content. However, it has…
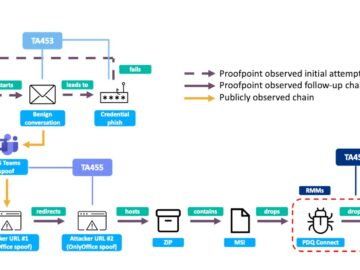
Proofpoint Threat Research has identified a previously unknown Iranian threat actor, dubbed UNK_SmudgedSerpent, that conducted sophisticated phishing campaigns against academics…
Security researchers have uncovered a sophisticated attack campaign attributed to Kimsuky, the North Korean-backed threat group known for conducting espionage…
Cisco has issued a critical security advisory addressing two severe vulnerabilities in its Unified Contact Center Express (CCX) platform that…
Cybersecurity researchers have discovered a resurgent Gootloader malware campaign employing sophisticated new evasion techniques that exploit ZIP archive manipulation to…